Scam Alerts
The Scam
Alerts page is designed to provide quick, brief updates on the latest scams.
Some of the topics will not deserve a page to themselves because they are so
small, whereas others will be covered in more detail elsewhere on the site.
The latest warnings are at the top of the page, and older items will drop
off the bottom into the archive links listed at the end of this page.
Bookmark this page and come back often
to read the updates.
CryptoWall Ransomware Schemes
Ransomware continues to spread and is infecting devices around the world. Recent IC3 reporting identifies CryptoWall as the most current and significant ransomware threat targeting individuals and businesses.
The financial impact to victims goes beyond the ransom fee itself, which is typically between $200 and $10,000. Many victims incur additional costs associated with network mitigation, network countermeasures, loss of productivity, legal fees, IT services, and/or the purchase of credit monitoring services for employees or customers.
Between April 2014 and June 2015, the IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million.
These financial fraud schemes target both individuals and businesses, are usually very successful, and have a significant impact on victims. The problem begins when the victim clicks on an infected advertisement, email, or attachment, or visits an infected website. Once the victim’s device is infected with the ransomware, the victim’s files become encrypted. In most cases, once the victim pays a ransom fee, he or she regains access to the files that were encrypted.
Most criminals involved in ransomware schemes demand payment in Bitcoin.
Criminals prefer Bitcoin because it's easy to use, fast, publicly available,
decentralized, and provides a sense of heightened security/anonymity.
Tips to protect yourself:
• Always use antivirus software and a firewall. It's important to obtain and use antivirus software and firewalls from reputable companies. It's also important to continually maintain both of these through automatic updates
• Enable popup blockers. Popups are regularly used by criminals to spread malicious software. To avoid accidental clicks on or within popups, it's best to prevent them from appearing in the first place
• Always back up the content on your computer. If you back up, verify, and maintain offline copies of your personal and application data, ransomware scams will have limited impact on you. If you are targeted, instead of worrying about paying a ransom to get your data back, you can simply have your system wiped clean and then reload your files
• Be skeptical. Don’t click on any emails or attachments you don't recognize, and avoid suspicious websites altogether.
If you receive a ransomware popup or message on your device alerting you to an infection, immediately disconnect from the Internet to avoid any additional infections or data losses. Alert your local law enforcement personnel and file a complaint at www.IC3.gov.
Gift Card Scam
The online presence of the Secondary Gift Card Market has grown significantly in recent years and provides a venue for consumers to resell unwanted gift cards. However, criminal activity has been identified through sites facilitating such exchanges.
There are both online and in-store venues for reselling gift cards. Kiosks and pawn shops are an option for consumers who prefer to handle a transaction in person. Secondary Gift Card Market websites exist to exclusively buy and sell gift cards.
Some of the various types of gift card scams reported are as follows:
- Victim sells a gift card on an auction site, receives payment for the sale, and sends the PIN associated with the gift card to the buyer, who disputes the charge after using the gift card
- Victim purchases an item on an auction site and is advised by the seller to purchase gift cards to pay for the transaction. After purchasing thousands of dollars in gift cards, the victim finds out the auction transaction is a scam
- A Secondary Gift Card Market site agrees to pay a victim for a discounted merchant gift card. The victim sends the code on the gift card, and the payment for the transaction was reversed. Thus, the buyer uses the gift card code to purchase an item and stops payment to the seller.
Consumers should beware of social media postings that appear to offer vouchers or gift cards, especially sites offering deals too good to be true, such as a free $500 gift card. Some fraudulent offers may pose as Holiday promotions or contests. The fraudulent postings often look as if a friend shared the link. Often these scams lead to online surveys designed to steal personal information. Never provide your personal information to an unknown party or untrustworthy website.
Tips to Prevent Gift Card Fraud:
Consumers can take several steps to protect themselves when buying and selling gift cards in the Secondary Gift Card Market, as listed below:
- Check Secondary Gift Card Market website reviews and only buy from or sell to reputable dealers
- Check the gift card balance before and after purchasing the card to verify the correct balance on the card
- The re-seller of a gift card is responsible for ensuring the correct balance is on the gift card, not the merchant whose name is on the gift card
- When selling a gift card through an online marketplace, do not provide the buyer with the card’s PIN until the transaction is complete. Online purchases can be made using the PIN without having the physical card
- When purchasing gift cards online, be wary of auction sites selling gift cards at a discount or in bulk
- When purchasing gift cards in a store, examine the protective scratch-off area on the back of the card for any evidence of tampering
Fake Government Websites
There have been complaints regarding criminals hosting fraudulent government services websites in order to acquire Personally Identifiable Information and to collect fraudulent fees from consumers.
The victims are having their Personally Identifiable Information data compromised which may be used by criminals for any number of other illegal activities, ranging from the creation of fraudulent IDs and passports to fraudulent loans and tax refunds. The Personally Identifiable Information can include the victim’s name, address, phone number, e-mail address, social security number, date of birth, and mother’s maiden name.
This is how the scheme usually works: victims use a search engine to search for government services such as obtaining an Employer Identification Number or replacement social security card. The fraudulent criminal websites are the first to appear in search results, prompting the victims to click on the fraudulent government services website. The victim completes the required fraudulently posted forms for the government service they need.
The victim submits the form online, believing they are providing their Personally Identifiable Information to government agencies such as the Internal Revenue Service, Social Security administration, or similar agency based on the service they need.
Once the forms are completed and submitted, the fraudulent website usually requires a fee to complete the service requested. The fees typically range from $29 to $199 based on the government service requested. Once the fees are paid the victim is notified they need to send their birth certificate, driver’s license, employee badge, or other personal items to a specified address.
The victim is then told to wait a few days to several weeks for processing. By the time the victim realizes it is a scam, they may have had extra charges billed to their credit/debit card, had a third-party designee added to their Employer Identification Number card, and never received the service(s) or documents requested.
Additionally, all of their Personally Identifiable Information data has been compromised by the criminals running the websites and can be used for any number of illegal purposes. The potential harm gets worse for those who send their birth certificate or other government-issued identification to the scammer.
Follow-up calls or e-mails to the scammers are normally ignored and many
victims report the customer service telephone numbers provided are out of
service. The FBI recommends that consumers ensure they are communicating or
requesting services/merchandise from a legitimate source by verifying the
entity. When dealing with government websites, look for the .gov domain
instead of a .com domain (e.g. www.ssa.gov and not www.ssa.com).
Below are some consumer tips when using government services or contacting agencies online:
- Use search engines or other websites to research the advertised services or person/company you plan to deal with
- Search the Internet for any negative feedback or reviews on the government services company, their Web site, their e-mail addresses, telephone numbers, or other searchable identifiers
- Research the company policies before completing a transaction
- Be cautious when surfing the Internet or responding to advertisements and special offers
- Be cautious when dealing with persons/companies from outside the country
- Maintain records for all online transactions.
Tax Return Fraud
Criminals are very good at stealing the personally identifiable information of individuals to carry out various fraud activities, including using stolen identity information to file fraudulent tax returns.
Once the scammers obtain victim information they electronically file tax returns and set up pre-paid debit cards or bank accounts to route fraudulent returns. The balances on the pre-paid cards and bank accounts are depleted shortly after the tax refund is issued.
The fraudsters utilize multiple methods to obtain the information needed to file a tax return. The most popular methods include: computer intrusion, the online purchase of stolen information, the recruitment of insiders who have legitimate access to sensitive information, the physical theft of computers that contain the information, the impersonation of Internal Revenue Service personnel, and the collection of information that is obtained through multiple publicly available Web sites.
Recently the cyber criminals have also targeted and compromised legitimate online tax software accounts of individuals. Cyber criminals conducting this scheme modify victims’ bank accounts to divert transfers to bank accounts or pre-paid cards under their control.Victims who filed complaints with the Internet Crime Complaint Center (IC3) reported they discovered they were victims of tax refund fraud when they tried to file a return and were notified by the Internal Revenue Service that their Social Security Numbers had already been used to file a tax return.
One individual reported that due to an error in direct deposit account information submitted on his return, he was issued a check. However, the victim had not yet filed a return. Others reported before they filed their return, they received notification that their returns were being audited or were under review.
A recent investigation identified a tax refund fraud ring responsible for filing approximately 644 fraudulent tax returns totalling over $1.9 million in attempted fraud. Using fraudulently obtained information, the fraudsters submitted tax returns and requested the funds be deposited into bank accounts under their control.
The group recruited college students to open accounts to collect the tax refund monies. The students withdrew funds via ATMs and counter withdrawals. The students then passed the majority of the funds to another group member and kept a portion of the refund as payment for the use of their bank accounts to conduct the scheme.
If you believe you have been a victim of this scam, you should reach out
to your local IRS or FBI field office, and you may file a complaint with the
IC3 at www.IC3.gov.
Tips to protect yourself:
* Monitor your credit statements for any fraudulent activity
* Report unauthorized transactions to your bank or credit card company as soon as possible
* Review a copy of your credit report at least once a year
* Be cautious of scams requiring you to provide your personal information
* Do not open email or attachments from unknown individuals
* Never provide credentials of any sort via email. This includes clicking on links sent via email * Always go to an official website
* If you use online tax services, double check to ensure your bank account is accurately listed before and after you file your tax return
* Ensure accounts that are no longer being utilized are properly deleted or scrubbed of sensitive information. Allowing online accounts to become dormant can be risky and make you more susceptible to tax fraud schemes.
Order Notification Emails
A series of 'order notification' emails are currently hitting inboxes. The emails thank you for purchasing and claim that your order is being processed. The emails do not name the company that supposedly sent the notifications. Nor do they say what product or service was supposedly purchased.
However, they do include an order total amounting to several thousand dollars along with an order number, order date and customer email address. They suggest that people check the attached file to find out more information about the purchase. The emails are formatted fairly professionally and may appear to be genuine at first glance.
Details such as subject lines, order totals, and attachment names may vary in different versions of the emails. Some have the subject line 'Urgent Notice'. Others may have the subject line 'Important Notification'.
However, the emails are not genuine order notifications and the order details included are not valid. The criminals responsible for the emails hope that at least a few recipients - panicked into believing that a large purchase has been made in their names - and will open the attachment without due caution.
However, the attached .zip file contains malware. If you unzip the attachment and then click the file inside, the malware may be installed on your computer.
The behaviour of the malware may vary based on the specific goals of the criminals who send it. The malware may collect sensitive information from the infected computer and relay it to scammers. It may also download further malware, and join the computer to a botnet.
Fake order receipt emails are a very common means of distributing malware. Be wary of any unsolicited email that claims to contain information regarding a purchase you know nothing about. If you receive such an email do not click any links or open any attachments that it contains.
Scammers May Use Paris Terrorist Attack to Solicit Fraudulent Donations
In the wake of the terrorist attack against Charlie Hebdo in Paris last month, the FBI is warning the public about fraudulent solicitations of donations for victims.
These solicitations come in many forms, such as crowdfunding platforms, e-mail campaigns, or cold calls, and scammers may divert some or all of the funds for their own use.
A number of charities and crowdfunding campaigns have already begun soliciting donations. In general individuals and businesses should be wary of suspicious e-mails, telephone calls, or websites that solicit donations in response to any event.
Crowdfunding—soliciting money from a large number of people primarily over the Internet—offers scammers a new venue to easily solicit funds with minimal oversight. Red flags to look out for include:
- The charity refuses to provide detailed information about its organization or how the donation will be used
- The charity uses a name closely resembling that of a reputable organization
- The charity pressures individuals to donate immediately
- The charity asks for donations to be sent through wire transfers, cash or virtual currency
- The charity guarantees a monetary return for a donation
The presence of one or more of these behaviours does not conclusively mean a charity is fraudulent; however, individuals and businesses should always verify a charity’s legitimacy before making any donations.
Donation Overpayment Scheme
There have been numerous complaints from businesses, charitable organizations, schools, universities, health related organizations, and non-profit organizations, reporting an online donation scheme.
The complaints reported subjects who had donated thousands of dollars, via stolen credit cards. Once donations were made, the subjects immediately requested the majority of the donation back, but credited to a different card. They claimed to have mistakenly donated too much by adding an extra digit to the dollar amount [i.e., $5000 was ‘accidentally’ entered instead of $500].
However, not many complainants actually returned the money to the second credit card.
Many, through their own investigations, discovered the original card was stolen, or the credit card company notified them of such. Also, some of the organizations’ policies did not allow funds to be returned to a different credit card.
Holiday Season Tips
If the deal sounds too good to be true, it probably is.
A reminder to shoppers in advance of the holiday shopping season to beware of cyber criminals and their aggressive and creative ways to steal money and personal information. Scammers use many techniques to defraud consumers by offering too good to be true deals via phishing e-mails advertising brand name merchandise, quick money making offers, or gift cards as an incentive to purchase a product. Remember, if the deal looks too good to be true, it probably is and never provide your personal information to an unknown party or untrusted website.
Scammers often use e-mail to advertise hot-ticket items of the year that may become hard to find during the holidays to lure unsuspecting consumers to click on links. Steer clear of untrusted sites or ads offering items at unrealistic discounts or with special coupons. You may end up paying for an item, giving away personal information and credit card details, and then receive nothing in return, along with your identity compromised. These sites may also be offering products at a great price, but the products being sold are not the same as the products they advertise. This is known as the bait and switch scam.
Beware of posts on social media sites that appear to offer vouchers or gift cards, especially sites offering deals too good to be true, such as a free $500 gift card. Some may pose as holiday promotions or contests. It may even appear one of your friends shared the link with you. If so, it is likely your friend was duped by the scam after it was sent to them by one of their friends. Oftentimes, these scams lead to online surveys designed to steal personal information. Remember, if the deal looks too good to be true, it probably is. And never provide your personal information to an unknown party or untrusted website.
When purchasing gift cards online, be wary of auction sites selling discounted or bulk offers of gift cards. When purchasing gift cards in the store, examine the protective scratch off area on the back of the card to see if it has been tampered with.
Be on the lookout for mobile applications designed to steal your personal information from your smartphone. Such apps are often disguised as games and are often offered for free. Research the company selling or giving away the app and look online for third party reviews before installing an app from an unknown source.
Tickets to theatre, concerts, and sporting events are always popular gifts during the holidays. If you purchase or receive tickets as a gift, do not post pictures of the tickets to social media sites. Protect the barcodes on tickets as you would your credit card number. Fraudsters will create a ticket using the barcode obtained from searching around social media sites and resell the ticket. You should never allow the barcode to be seen on social media.
If you are in need of extra cash at this time of year, beware of sites and posts offering work you can do from the comfort of your own home. Often, the work from home opportunities rely on convenience as a selling point for applicants with an unscrupulous motivation behind the posting. You should carefully research the job posting and individuals or company contacting you for employment.
As a consumer, if you feel you are a victim of an Internet-related crime, you may file a complaint with the FBI’s Internet Crime Complaint Center at www.IC3.gov.
Tips
Here are some additional tips you can use to avoid becoming a victim of cyber fraud:
- Check your credit card statement routinely
- Protect your credit card numbers from “wandering eyes”
- Do not respond to unsolicited (spam) e-mail
- Do not click on links contained within an unsolicited e-mail
- Be cautious of e-mail claiming to contain pictures in attached files, as the files may contain viruses. Only open attachments from known senders. Scan the attachments for viruses if possible
- Avoid filling out forms contained in e-mail messages that ask for personal information
- Always compare the link in the e-mail to the link you are actually directed to and determine if they actually match and lead you to a legitimate site
- Log on directly to the official website for the business identified in the e-mail, instead of “linking” to it from an unsolicited e-mail. If the e-mail appears to be from your bank, credit card issuer, or other company you deal with frequently, your statements or official correspondence from the business will provide the proper contact information
- If you are requested to act quickly or there is an emergency, it may be a scam. Fraudsters create a sense of urgency to get you to act quickly
- Verify any requests for personal information from any business or financial institution by contacting them using the main contact information on their official website
- Remember if it looks too good to be true, it probably is.
False Advertisements
Be aware of criminals targeting online consumers by posting false advertisements for high priced items such as automobiles, boats, heavy equipment, recreational vehicles, lawn mowers, tractors, and other similar items.
The scam initiates when the criminals post a false advertisement offering the item for sale. The advertisement usually includes a fraudulent photo to entice the consumer to purchase the item. Within the advertisement, the criminal includes a contact telephone number. The consumer leaves a message and the scammer responds via text message.
The text message normally requests that the consumer provide an e-mail address. Once the e-mail address is provided the consumer is sent additional details to include multiple images of the item for sale. The scammer provides logical reasons for offering the item at such a discounted price such as moving to another location; therefore, the item needs to be sold quickly; the sale was part of a divorce settlement; or overseas deployment.
Consumers normally negotiate a price. Many scammers advise the consumer the transaction will be conducted through Ebay to ensure a safe and easy transaction. In reality the scammer is only pretending to use Ebay. The consumer receives a false e-mail that appears to be legitimate from Ebay.
The e-mail provides instructions on how to complete the transaction. The scammer provides the consumer with all the information necessary to complete the wire transfer - the bank account name, address, and account number. The scammer provides a fraudulent toll-free Ebay customer service number for the consumer to use when they are ready to wire the money.
These numbers were also used by many victims to confirm a successful wire transfer or to check transaction status and shipping information. After the transaction, the consumer is sent a false Ebay confirmation e-mail that includes the fraudulent transaction or confirmation number and the expected delivery date of the item.
Any follow-up calls, text messages or e-mails to the scammer(s) are normally ignored and many victims report the toll-free customer service telephone numbers provided are constantly busy. As a result, the consumer never receives the purchased item(s) and suffers a financial loss.
Consumers are advised to ensure they are purchasing the actual merchandise from a reputable source by verifying the legitimacy of the seller. Below are some consumer tips when purchasing items online:
- Use search engines or other websites to research the advertised item or person/company selling the item
- Search the Internet for any negative feedback or reviews on the seller, their e-mail addresses, telephone numbers, or other searchable identifiers
- Research the company policies before completing a transaction. For example, ensure the seller accepts payments via credit card as Ebay does not conduct wire transfers and only uses PayPal to conduct transactions
- Be cautious when responding to advertisements and special offers
- Be cautious when dealing with persons/companies from outside the country
- Maintain records for all online transactions
Green Dot MoneyPak Customer Support Scam
There have been numerous complaints reporting fraudulent websites posing as MoneyPak customer support. MoneyPak is a non-reloadable, prepaid product offered by Green Dot.
Complaints indicate victims locate the websites via Internet search engines. Interaction between the victims and the fraudulent customer support generally occurs via telephone. There have been variations of this scam.
- The victim is seeking a refund from an already purchased MoneyPak card and contacts the information listed on the website. A customer service “representative” will ask the caller to provide the identification number of the prepaid card. ◦Example – The victim loaded funds onto a MoneyPak card and now wishes to receive a refund of those funds off of the prepaid card. The representative will ask for the prepaid card number and a credit card or checking account number to which the refund can be processed. At this point, the scammer has access to the funds on the prepaid card and the victim’s personal account.
- Victim seeks support in connection with loss from other possible scams. The representative will instruct the caller to re-load the card with additional funds equal to the previously lost amount. ◦Example – The victim lost $500 from their MoneyPak card to a separate scam and is seeking a refund to the card. The representative will instruct the victim to load an additional $500 to the card. The representative states “re-loading is the only way to process the refund”, and the card will be refunded the full $1,000. Should the victim refuse to re-load the card, the representative will promptly disconnect the call.
In most complaints, victims are given a tracking or confirmation number in connection with their call and report to be placed “on hold” for a length of time while the representative claims to be researching the problem regarding the card in question.
In all complaints, any funds available on the card are drained while the victim is on hold or immediately after the call is disconnected.
Consumer Protection
Consumers should only use the website and phone number listed on the back of the MoneyPak prepaid cards. MoneyPak customer support can only be accessed by email request via the website’s online portal. The phone number listed on the back of MoneyPak cards is for adding funds to an existing prepaid card.
Green Dot customer service publicizes a customer service number; however, this number will not provide assistance with MoneyPak.
Currently identified fraudulent websites are not secured websites (http).The MoneyPak customer support website is a secured website (https) and does not require personal (date of birth, social security number) to reload a card, add money to PayPal or make payments to authorized partners. Prepaid card information is needed to reload a prepaid card on the valid MoneyPak website. Visit https://www.moneypak.com/ for more information.
Filing A Complaint
Individuals who believe they are a victim of a “MoneyPak Support” scam can file with the IC3 at http://www.ic3.gov. Please be as descriptive as possible, including prepaid card/account numbers affected and contact information of support “representatives”.
Because scams and fraudulent websites appear very quickly, individuals are encouraged to report possible internet scams and fraudulent websites by filing a complaint with the IC3 at http://www.ic3.gov.
Additional Information From MoneyPak.1
How to Stop A Scam
Tips On How To Protect Yourself From Fraud
- Never give your MoneyPak number to someone you don’t know
- Never give receipt information about your MoneyPak purchase to another party
- Use your MoneyPak only to reload your prepaid cards or accounts you control
- Refuse any offer that asks you to buy a MoneyPak and share the number or receipt information by email or phone
- To use your MoneyPak with PayPal or eBay or other online merchants, transfer the money to your PayPal account before you pay the merchant. Don’t email your MoneyPak number directly to any merchant
- Unless it’s an approved MoneyPak partner, don’t use MoneyPak for any offer that requires you to pay before you get the item
StealthGenie Mobile Device Spyware Application
StealthGenie is a mobile device spyware application (“app”) that is alleged to illegally intercept wire and electronic communications made using mobile phones.
What are mobile device spyware apps?
Mobile device spyware apps are developed for smart mobile phones and may allow a purchaser of the app to, amongst other things, secretly monitor a phone user’s communications and whereabouts. The purchaser must generally have physical access to a target mobile phone to install a mobile device spyware app, which is usually downloaded to the phone. Each phone software platform, such as Apple Inc.’s (“Apple”) iOs (for iPhones) and Google Inc.’s (“Google”) Android, require specific steps to complete the installation process.
How does StealthGenie work?
The StealthGenie app works in so-called “stealth” mode and is undetectable by most individuals. It is advertised as being untraceable. StealthGenie’s capabilities include the following:
- Call Recording: Records all incoming/outgoing voice calls or those specified by the purchaser of the app
- Call Interception: Allows the purchaser to intercept calls on the phone to be monitored while they take place, without the knowledge of the monitored smartphone user
- Recorded Surroundings: Allows the purchaser to call the phone and activate it at any time to monitor all surrounding conversations within a fifteen (15)-foot radius without the knowledge of the user
- Electronic Mail: Allows the purchaser to monitor the incoming and outgoing e-mail messages of user, read their saved drafts, and view attachments
- SMS: Allows the purchaser to monitor the user’s incoming and outgoing SMS messages
- Voicemail: Allows the purchaser to monitor the incoming voicemail messages
- Contacts: Allows the purchaser to monitor the entries in the user’s address book
- Photos: Allows the purchaser to monitor the photos on the user’s phone
- Videos: Allows the purchaser to monitor the videos on the user’s phone
- Appointments: Allows the purchaser to monitor the user’s calendar entries
The purchaser can review information transferred from the target mobile phone via an online portal. These intercepted communications are stored on the StealthGenie website. For example, a purchaser can log-in to the online portal to access information pulled from the user’s phone such as messages, e-mail, photos, and phone calls.
Can a person tell if a mobile device spyware app is on his or her phone?
Mobile device spyware apps are developed and advertised as being invisible to targets and act in an undetectable manner. For example, an app can be installed to look like another type of app or file, such as a digital photo application. Therefore, it will be difficult for the non-expert user to determine whether or not spyware is on his or her phone.
If a user is concerned about the potential presence of a mobile device spyware app on their phone, the only way to ensure that any app is permanently removed from the phone is to perform a “factory reset,” as described immediately below.
How can a mobile device spyware app be removed?
If you believe your phone may contain a mobile device spyware app, the best option is to conduct a “factory reset” of the phone. When a reset takes place, the phone is restored to its original condition (i.e., the condition at the time of purchase).
Please be advised that this means any and all data and apps installed after purchase will be removed from the phone, including all stored information. Please make sure to back-up any data you want to save from your phone before conducting a factory reset. Please note that performing a factory reset of a phone will not delete any information that has already been already collected from the phone by the mobile device spyware app from a vendor’s website.
Apple has provided information concerning how to perform a factory reset of an iPhone running the latest version of their mobile device operating system at http://support.apple.com/kb/HT1414 .
Because Google’s Android operating system is customizable by a phone manufacturer, please contact your phone’s manufacturer for instructions on how to factory reset your phone, or take it to the store from which you purchased the phone. Similar action should be taken to determine how to factory reset a non-iPhone or non-Android phone.
IRS Telephone Scam
There are reports related to a telephone scam in which the caller claims to be an Internal Revenue Service (IRS)representative. Using intimidation tactics, the caller tries to take control of the situation from the beginning.
The caller advises the recipient of the call that the IRS has charges against them and threatens legal action and arrest. If the recipient questions the caller in any way, the caller becomes more aggressive.
The caller continues to intimidate by threatening to confiscate the recipient’s property, freeze bank accounts, and have the recipient arrested and placed in jail. The reported alleged charges include defrauding the government, money owed for back taxes, law suits pending against the recipient, and non-payment of taxes.
The recipients are advised that it will cost thousands of dollars in fees/court costs to resolve this matter. The caller creates a sense of urgency by saying that being arrested can be avoided and fees reduced if the recipient purchases Moneypak cards to cover the fees within an hour.
Sometimes the caller provides specific instructions on where to purchase the Moneypak cards and the amount to put on each card. The caller tells the recipient not to tell anyone about the issue and to remain on the telephone until the Moneypak cards are purchased and the Moneypak codes are provided to the caller. The caller states that if the call is disconnected for any reason, the recipient would be arrested.
Some recipients reported once the caller obtained the Moneypak codes, they were advised that the transaction took too long and additional fees were required. Call recipients, who are primarily immigrants, reported that the caller spoke with broken English or stated the caller had an Indian accent.
If you receive a call similar to this follow these tips:
• Resist the pressure to act quickly
• Report the contact to TIGTA at http://www.treasury.gov/tigta by clicking on the red button, “IRS Impersonation Scam Reporting”
• Use caution when asked to use a specific payment method. The IRS would not require a specific payment method such as a Moneypak card or wire transfer
• If you feel threatened, contact your local police department
• File a complaint at www.IC3.gov
Internet Crime Complaint Center Scam
Cyber criminals posing as Internet Crime Complaint Center (IC3) employees are defrauding the public. The IC3 has received complaints from victims who were receiving e-mails claiming to be from the IC3.
Victims report that the unsolicited e-mail sender is a representative of the IC3. The e-mails state that a criminal report was filed on the victim’s name and social security number and legal papers are pending. Scammers impersonate an IC3 employee to increase credibility and use threats of legal action to create a sense of urgency. Victims are informed they have one to two days from the date of the complaint to contact the scammers.
Failure to respond to the e-mail will result in an arrest warrant issued to the victim.
Some victims stated they were provided further details regarding the ‘criminal charges’ to include violations of federal banking regulations, collateral check fraud, and theft deception. Other victims claimed that their address was correct but their social security number was incorrect. Victims that requested additional information from the scammer were instructed to obtain prepaid money cards to avoid legal action. Victims have reported this scam in multiple states.
If you receive this type of e-mail:
• Resist the pressure to act quickly
• Never wire money based on a telephone request or in an e-mail, especially to an overseas location
The IC3 never charges the public for filing a complaint and will never threaten to have them arrested if they do not respond to an e-mail.School Impersonation Scam
Subjects posing as school officials are defrauding retailers by purchasing large volumes of merchandise using fraudulently obtained lines of credit. Originally this scheme affected mostly office suppliers and computer retailers; however, recent successful attempts lead subjects to use this scheme against other retailers for industrial equipment, pharmaceuticals, safety and medical equipment.
How the Scheme Works
Step 1: A subject, posing as a school official, contacts a retailer’s customer service call center by telephone or e-mail. Using social engineering tactics, the subject attempts to gather additional information about the purchasing account. The subject typically terminates the phone call or e-mail session once sufficient information is gathered to place an order. Subjects also obtain account information from the school’s public website, if available.
Step 2: The subject makes a second contact with the target vendor, again representing himself as a school official and providing the account information obtained from step one. Billing to the school’s line of credit, the subject makes large purchases (such as laptops, routers, hard drives, printer toner, printer ink, medical supplies, and industrial equipment) with some orders totalling more than $200,000.
Step 3: During the purchase, the subject provides the customer service representative with a U.S. shipping address, typically belonging to a victim of a “romance scam” or “work from home” fraud scheme. A subject contacts the online scam victim and directs the individual to re-ship the office supplies to an address in West Africa, typically Nigeria, the United Kingdom, or to a U.S.-based storage or warehouse facility. To facilitate the re-shipment, the individual receives a shipping label prior to receiving the merchandise.
In a more recent variation of the scheme, the subject provides the true shipping address of the school he is claiming to represent. The subject then contacts the school, posing as an employee of the vendor, claiming that the products were shipped to the school in error. The school, believing it is returning the products to their rightful owner, reships the items to a domestic address provided by the subject.
Recruited individuals in the U.S. then re-ship the products overseas. What started with a small number of educational institutions has rapidly spread through copycatting and spoofing techniques to include some complaints reporting businesses instead of schools or universities being victimized.
E-mail Account Spoofing Techniques are used by subjects to place orders by establishing false school e-mail accounts, which appear similar to legitimate school e-mail addresses but lack the .edu extension. Below are variations of spoof email addresses:
• purchasingdept@unlav-edu.org
Once the fraud is discovered, the retailer absorbs the financial losses without recourse to the school.
To recruit the re-shippers, a subject, posing as an employer or romantic interest, gains the trust of individuals searching for employment opportunities or a romantic relationship. After a period of social engineering, the individuals are convinced to serve as money remitters or re-shippers on behalf of the subject.
Netflix Account Cancellation Scam
You may have recently received an account cancellation message claiming to be from online video streaming service Netflix. The message claims that, because of a problem processing your credit card, you must click a link to update card details to keep your account active.
The message is not from Netflix and you do not need to update credit card details as claimed. The message is a typical phishing scam and attempts to steal Login and Credit Card Details.
Clicking the 'update link' will take you to a fake webpage designed to look like the genuine Netflix site. Once on the fake page, you will be asked to provide your account login details, your credit card details, and, possibly, other personal information as well.
Online criminals will collect all of the information you submit on the fake page and can now commit credit card fraud in your name and gain access to your Netflix account. If they have been able to harvest enough of your personal information, they may also be able to steal your identity.
Phishing scammers regularly target Netflix customers and this version is just one of many similar phishing campaigns that have tried to trick Netflix customers into parting with their personal and financial information.
Be Cautious of 'Account Update' Messages.
Be wary of any unsolicited Netflix message that claims that you must update account details, rectify a billing issue, or prove your identity for security purposes.
And, scammers use very similar tactics to target customers of many other popular online services. If you receive such an 'update' message, do not click any links or open any attached file that it contains.
Don't Click Email 'Login' Links.
It is best not to click login links in emails. It is safest to login to all
of your online accounts by entering the account address into your browser's
address bar or via a trusted application associated with the service.
Google+ Scam
You may receive a poorly written phishing email claiming to be from the 'All Domain Mail Team' at Google's social network Google+.
It claims that the team is running a 'spam and fraudulent verification survey' and asks users to click a link to participate. It warns that if the verification survey is 'not gotten' within 24 hours, the team will assume that the recipient is a 'fraulent user' and his or her email account will be shut down.
The first sign that this is a scam email is the poor spelling and strange grammar. Another indicator would be that common sense would indicate that staff at Google+ would not be responsible for overseeing email security measures. Nor would they have the power to shut down email accounts. Maybe the scammers meant to specify 'Gmail' instead of 'Google+'.
If you click on the link it opens a website that simply requests users to login with their Google email address and password, supposedly to complete the verification process.
The login details will be collected by criminals and used to hijack the Google accounts belonging to the victims. The one set of login credentials can be used to access many different Google services. Thus, the criminals may be able to steal private information stored in various Google applications as well as use Gmail and Google+ accounts to launch further spam and scam campaigns.
Phishing scammers often try to trick users into submitting login details and other personal information by claiming that account details must be verified to improve security. Be wary of any unsolicited email that claims that you must click a link to verify or update your account or risk account suspension.
If you get one of these messages, do not click any links or open any attachments that it contains.Business Email Compromise
We been receiving complaints from businesses that were contacted fraudulently via legitimate suppliers’ e-mail accounts. Recipients were asked to change the wire transfer payment of invoices. Businesses became aware of the scheme after the legitimate supplier delivered the merchandise and requested payment. This scam has been referred to as the “business e-mail compromise.”
A twist to this scam that is being reported relates to the spoofed business e-mail accounts requesting unauthorized wire transfers. In the scheme, a business partner, usually chief technology officers, chief financial officers, or comptrollers, receives an e-mail via their business accounts supposedly from a vendor requesting a wire transfer to a designated bank account. The e-mails are spoofed by adding, removing, or subtly changing characters in the e-mail address that make it difficult to identify the perpetrator’s e-mail address from the legitimate address.
The scheme is usually not detected until the company’s internal fraud detections alert victims to the request or company executives talk to each other to verify the transfer was made.
The average dollar loss per victim is approximately $55,000. However, the IC3 has received complaints reporting losses that exceed $800,000.
There have been complaints from companies that were alerted by their suppliers about spoofed e-mails received using the company’s name to request quotes and/or orders for supplies and goods. These spoofed e-mails were sent to multiple suppliers at the same time. In some cases, the e-mails could be linked by Internet Protocol (IP) address to the original business e-mail compromise scams.
Because this latest twist is relatively new, the dollar loss has not been significant. Also, victim companies have a greater chance of discovering the scheme because the e-mails go to multiple suppliers that often follow-up with the company.
Based on analysis of the complaints, the scam appears to be Nigerian-based. Complaints filed contain little information about the perpetrators. However, subject information that was provided has linked to names, telephone numbers, IP addresses and bank accounts reported in previous complaints, which were tied over the years to traditional Nigerian scams.
Some commonalities found among the complaints include:
1. Victims are generally from the United States, England and Canada, although there have been complaints from other countries such as Belgium
2. Victim businesses often trade internationally, usually through China
3. Victim businesses that conduct high-dollar wire transfers, so requests for larger monetary amounts are not uncommonVisa Card Status Notification Scam
There is an email circulating that appears to be a 'Visa Card Status Notification' advising that access to the recipient's Visa card has been blocked. The message states that the account limits have been implemented because the Visa Card security department identified some unusual activity on the card.
The message invites the card owner to click on a link to resolve the issue and restore access.
The message is not from Visa and the claim that the account has been limited is not true. The email is a typical phishing scam designed to extract financial information from card owners.
The email's links open a fake website created to closely look like a genuine Visa webpage. The fake page will include a 'verification form' that requests users to supply their credit card number and other account details. After supplying the requested information, users will be taken to a second fake page that informs them that the problem has been resolved and restrictions have been removed.
Then victims may go about their business in the mistaken belief that they have rectified the problem with their card and all is well, however there was never any problem with the card to begin with. The criminals who have the card holders details can now commit fraudulent transactions via the Visa accounts of their victims.
These phishing scams are very common and continually target customers of major credit card providers and financial institutions all around the world. A well-worn phishing tactic is to claim that the recipient's account has been blocked or suspended and will claim that users can resolve this block by clicking a link - or in some cases opening an attached file - and filling in a verification form.
If you receive such an email, do not click any links or open any attachments that it contains.
Walmart Voucher Scam
An email being circulated claims you have accumulated $500 worth of Wal-Mart vouchers that have not yet been claimed. Supposedly, the vouchers were not sent because you have not confirmed your account details.
The message asks you to follow a link and supply your personal information so that the vouchers can be mailed out. Strangely, the message signs off as being from 'Tesco Personal Finance'.
However, the email is not from Wal-Mart (or Tesco) and the promised vouchers do not exist. If you click the link to claim the promised vouchers you will be taken to a fake web form that asks for your name and address details, social security number, phone number and email address. After supplying this information and pressing the 'Submit' button, you will be informed that the update process is complete and that the vouchers will be mailed to you in the next few days.
But, the vouchers will never come, and the criminals have already started accumulating personal information that may subsequently be used to commit identity theft and financial fraud.
The scammers now know a very valuable fact about the people who replied because they know they are vulnerable to falling for these types of scams and so may be directly targeted in further scams. They may receive 'follow up' emails that ask for more personal details and financial information such as credit card numbers.
Because the scammers now have the names and other personal data belonging to their victims, they can carry out personalized and specifically targeted phishing attacks that may appear quite legitimate.
The promise of unclaimed vouchers is a common scam so be wary of any message that suggests that you can claim unexpected vouchers or gift cards by clicking a link or opening an attached file and supplying personal information.
University Scam
There have recently been multiple scams targeting universities, university employees, and students across the USA. The scams range from Internet fraud to intrusions. The following are common scenarios:
• Spear phishing emails are being sent to university employees that appear to be from their employer. The email contains a link and claims some type of issue has risen requiring them to enter their log-in credentials. Once employees provide their user name and password, the scammer accesses the university’s computer system to redirect the employees’ payroll allocation to another bank account. The university employees’ payroll allocations are being deposited into students’ accounts. These students were hired through online advertisements for work-at-home jobs, and provided their bank account information to the scammers to receive payment for the work they performed
• Scammers are posting online advertisements soliciting college students for administrative positions in which they would receive checks via the mail or email. Students are directed to deposit the checks into their accounts, and then print checks and/or wire money to an individual. Students are never asked to provide their bank account information to the scammers
• Scammers are compromising students’ credentials resulting in the re-routing of their reimbursement money to other bank accounts. The reimbursement money is from student loans and used to pay tuition, books, and living expenses
• Scammers are obtaining professors’ Personally Identifiable Information (PII) and using it to file fraudulent income tax returns
• Some universities have been victims of intrusions, resulting in the scammers being able to access university databases containing information on their employees and students
Amazon Scam
There is an email circulating that claims to be from Amazon, and that it performs 'integrity checks' on customer accounts every six months. It claims that, if a customer's account is not used for longer than one month, it will first be disabled and then - after two months - removed completely.
To prevent this supposed problem, the message instructs customers to click a 'one time use' validation link, however the email warns the customer that the link is only active for 24 hours and if customers fail to 'make verification' within that time frame, their accounts will be disabled.
The email is not from Amazon and the claims are fake so the recipient does not need to click on the link. The message is a phishing scam designed to trick users into relinquishing their personal and financial data to Internet criminals.
The links in these scam messages typically lead to a fake webpage designed to look like a genuine Amazon page. The fake page asks users to provide their Amazon account login details as part of the verification process. After 'logging in' on the fake site, users may be taken to a second page that asks for their credit card details and other personal and financial information. If they supply the requested information, users may then receive a message claiming that their validation has been successful.
The scammers have now collected the information submitted on the fake forms and can use it to hijack Amazon accounts and commit credit card fraud.
A big warning sign in the email is the poor spelling and grammar. Amazon carries out most of its business online, so it is regularly targeted by phishing scammers.
Telephone Scam Alleging A Relative Is In A Financial Or Legal Crisis
There continues to be reports of telephone scams involving calls that claim their “relative” is in a legal or financial crisis. These complaints are sometimes referred to as the “Grandparent Scam.”
Scammers use scenarios that include claims of a relative being arrested or in a car accident in another country. Scammers often pose as the relative, create a sense of urgency and make a desperate plea for money to victims.
It is not unusual for scammers to beg victims not to tell other family members about the situation.
The scammers also impersonate third parties, such as an attorney, law enforcement officer, or some other type of official, such as a U.S. Embassy representative. Once potential victims appear to believe the caller’s story, they are provided instructions to wire money to an individual, often referred to as a bail bondsman, for their relative to be released.
Some complainants have reported the callers claimed to be from countries including, but not limited to: Canada, Mexico, Haiti, Guatemala, and Peru. Callers often disguise themselves by using telephone numbers generated by free applications or by spoofing their numbers.
If you receive this type of call:
• Resist the pressure to act quickly
• Verify the information before sending any money by attempting to contact your relative to determine whether or not the call is legitimate
• Never wire money based on a request made over the phone or in an e-mail, especially to an overseas location. Wiring money is like giving cash—once you send it, you cannot get it back.
Human Hair Scam
The demand for long hair, new hair styles, or hair to conceal a medical condition associated with hair loss is nothing new; however, it does appear the exploitation of human hair is on the rise.
Human hair is sometimes preferred by consumers over synthetic hair due to the natural look, feel, styling versatility, and longevity. Based on analysis of recent targets, it appears there is a fairly consistent overlap in the sale of human hair on websites that also sell counterfeit wearing apparel commodities.
A recent target domain was involved in the sale of counterfeit wedding dresses imported from China, as well as advertising human hair. This assessment identified 132 connected domain names referencing brand name shoes, bags, and dresses. An additional subject was also accused of selling fake hair, designer handbags, brand gym shoes, and boots.
Additionally, a company in China, selling counterfeit brand name shoes, advertises Peruvian, Brazilian, Indian, and Malaysian virgin hair. Virgin hair refers to hair that is completely unprocessed and intact. To qualify as virgin hair, it must meet rigorous standards including; not been permed, dyed, colored, bleached, or chemically processed in any way.
This also means it comes from a single donor, and all the cuticles are intact, running in the same direction. Usually, it also means that is has not been blow-dried, or exposed to harsh agents such as cigarette smoke and drugs.
The hair is being advertised as human; however, consumers are receiving synthetic hair after paying a substantially higher price for this authentic commodity.
Be sure to check the authenticity of the hair as well as the seller.
Callback Scheme In International Revenue Share Fraud
Telephone companies in the United States are seeing missed calls used to enable International Revenue Share Fraud (IRSF).
Fraudsters are using call generators with automated spoofing capabilities to place calls to a large volume of US cell phone numbers. The calls typically ring once. The number displayed on the recipient’s caller ID is a high cost international number, usually located in the Caribbean.
The recipient calls the number back and is greeted with a message designed to keep them on the line, such as “Hello, you have reached the operator, please hold.” The longer the caller stays on the line, the more revenue fraudsters generate.
Recipients do not realize they are calling an international number and that they will be billed for an international call. Businesses are also victims because recipients often use their work telephone to make the return call.
Telephone companies in the United States are charged when a return call is made because they are required to pay a fee to transfer calls to foreign countries. The payment is then shared with the fraudster who spoofed the calls. This is referred to as IRSF.
Area codes used in the spoofed numbers are from Anguilla, Antigua, Barbados, British Virgin Islands, the Commonwealth of Dominica, Grenada, Montserrat, and the Turks and Caicos Islands. These countries’ numbers are part of the North American Numbering Plan and do not require 011 to be dialed as with other international calls.
Recipients should not answer calls from numbers they do not recognize or initiate a return call. Recipients will not be charged for receiving the calls, however.
Companies that do not conduct business with companies in the above-mentioned countries may want to consider blocking these area codes to avoid this type of charge.Reshipping Job Opportunity
The job might look like a great opportunity, especially if you are unemployed. According to the job descriptions, which typically arrive via email or in response to a job profile posted online, all the job applicants need do to earn a generous wage is receive items, repackage them, and send them off to specified addresses.
However, the supposed job is in fact a reshipping scam designed to trick users into receiving the proceeds of crime. What the worker will actually be doing is accepting goods bought via fraudulent transactions and sending them back to the criminals responsible for the scam.
Why? Because, if a criminal steals your credit card details and uses them to buy various items, they need to have the items delivered somewhere and can't just have them delivered to their own address, because that could pinpoint their location to investigators and result in their arrest.
So, instead, the criminal needs to find a parcel mule to accept the fraudulently purchased items on their behalf. When police follow the trail, they will arrive at the door of the mule, not the real offender. Meanwhile, the criminal has had their goods shipped to themselves or more likely, sell them for cash.
In order to successfully purchase expensive merchandise with stolen payment cards and later sell for cash, fraudsters have to ensure that the mailing address matches the billing address. This obstacle is usually easily overcome by changing the billing address of stolen cards to the addresses of their hired, pre-assigned mules.
Another challenge for fraudsters in managing a successful reshipping operation is obtaining a seemingly innocent “drop” address where mules dwell. The most effective way to overcome this challenge is to recruit and hire mules that live in the United States. The United States is a strategic location for fraudsters in which to base their reshipping scams as many major online merchants who sell popular high-value goods do not ship their items outside of that country.
The reshipping mules can find themselves trapped inside the scam and at a loss as to how to get out. After a time, they may realize that they are involved in a scam, but by then, they may be scared to contact authorities out of fear of being charged with criminal activities, as well as their criminal "bosses" may threaten violence and retaliation to victims who try to get out themselves.
To make matters worse, the criminals may "pay" their mules with fake or stolen cheques or funds transferred from compromised accounts. They may instruct workers to deduct their wages and wire a remaining amount via a money transfer service such as Western Union. Thus, workers may be roped into laundering money as well as receiving stolen goods.
And mules are sometimes tricked into paying postage and other costs out of their own pockets, with a false promise that they will be later reimbursed.
In a variation of the tactic, criminals may find new and willing victims via online dating scams.
Be wary of any work-at-home job that requires you to receive various goods and reship them elsewhere. Any such request should be treated as suspect. If you have already become caught up in a parcel mule scam, you need to get yourself out immediately. The best course of action is to contact police and explain the situation.
Better than waiting for the police to arrive on your doorstep.
Holiday Shopping Tips
With the holiday season coming up, it is a timely reminder for holiday shoppers to beware of cyber criminals who are out to steal money and personal information. Scammers use many techniques to defraud you, from phishing e-mails offering too good to be true deals on brand-name merchandise to offering quick cash to victims who will re-ship packages to additional destinations.
While monitoring credit reports on an annual basis and reviewing account statements each month is always a good idea, you should keep a particularly watchful eye on your personal credit information at this time of year. Scrutinizing credit card bills for any fraudulent activity can help to minimize your losses. Unrecognizable charges listed on a credit card statement are often the first time you realize your personally identifiable information has been stolen.
Bank transactions and correspondence from financial institutions should also be closely reviewed. Bank accounts can often serve as a target for criminals to initiate account takeovers or commit identity theft by creating new accounts in your name. You should never click on a link embedded in an e-mail from your bank, but rather open a new webpage and manually enter the URL (web address), because phishing scams often start with phony e-mails that feature the bank’s name and logo.
When shopping online, make sure to use reputable sites. Often consumers are shown specials on the web, or even in e-mail offers, that look too good to be true. These sites are used to capture personally identifiable information, including credit card numbers, addresses and phone numbers to make fraudulent transactions. It’s best to shop on sites with which you are familiar and that have an established reputation as trusted online retailers, according to the MRC, a nonprofit that supports and promotes operational excellence for fraud, payments and risk professionals within eCommerce.
If you look for an item or company name through a search engine site, scrutinize the results listed before going to a website. Do not automatically click on the first result, even if it looks identical or similar to the desired result. Many fraudsters go to extreme lengths to have their own website appear ahead of a legitimate company on popular search engines. Their website may be a mirrored version of a popular website, but with a slightly different URL.
Purchases made on these sites could result in one or more of the following consequences: never receiving the item, having your credit card details stolen, or downloading malware/computer virus to your computer. Before clicking on a result in a search engine, inspect the URL of the destination website. Look for any misspellings or extra characters such as a period or comma as these are indicative of fraud. When taken to the payment page of a website, again verify the URL and ensure it is secure by starting with “HTTPS,” not just “HTTP.”
Here are some additional tips you can use to avoid becoming a victim of cyber fraud:
• Do not respond to unsolicited (spam) e-mail
• Do not click on links contained within an unsolicited e-mail
• Be cautious of e-mail claiming to contain pictures in attached files; the files may contain viruses. Only open attachments from known senders. Scan the attachments for viruses if possible
• Avoid filling out forms contained in e-mail messages that ask for personal information
• Always compare the link in the e-mail to the link you are actually directed to and determine if they match and will lead you to a legitimate site
• Log on directly to the official website for the business identified in the e-mail instead of “linking” to it from an unsolicited e-mail. If the e-mail appears to be from your bank, credit card issuer, or other company you deal with frequently, your statements or official correspondence from the business will provide the proper contact information
• Contact the actual business that supposedly sent the e-mail to verify that the e-mail is genuine
• If you are requested to act quickly or there is an emergency that requires your attention, it may be a scam. Fraudsters create a sense of urgency to get you to act quickly
• Remember if it looks too good to be true, it probably is.
Quantas Employment Scam
You may receive an email that appears to come from the Australian airline Qantas, advising you that the company currently has job vacancies in a range of areas. Interested applicants are invited to send their resumes to an email address listed in the message.
However, the email is not from Qantas and is an attempt to trick job hunters into making contact with online criminals. If you apply and send your resume you will soon receive a reply offering you a position with the company. The reply talks in glowing terms of excellent working conditions and high wages.
The message will also claim that, before you can start the exciting new job, certain prerequisites will need to be met. You will be told that you must pay upfront fees to cover various expenses such as a police or security clearance, training material, uniforms or equipment. Or you may be asked to send money so that the airline can arrange accommodation and travel for you. You may be told that the company will later reimburse any upfront fees you send.
Further requests for fees will continue until you finally realize that this is a scam, or you run out of funds to send. You will also be asked to provide a large amount of personal and financial information to verify your identity and allow you to be put on the company payroll. The information you provide may later be used to steal your identity.
In recent months, similar scam campaigns have claimed to offer jobs at various other high profile companies such as Disney Cruise Line, Radisson and Hilton.
Be wary of any unsolicited email offering you a job at a well-known company. In an attempt to make the emails look genuine, they often include stolen company logos as well as links that point to the genuine company website. Sometimes, they may also copy text from career information published on the company's website.However, large companies are very unlikely to send out bulk unsolicited job emails, and they certainly wouldn't do it via a free online webmail service rather than their own company domain.
Apple Account Frozen
You may receive an email which claims to be from Apple, stating that your Apple account has been frozen temporarily in order to protect it. The message warns that, unless you open an attached file to validate account information, the account will remain frozen.
However, your account has not been frozen. The email is the work of criminals intent on robbing you of your personal and financial data.
If you get taken in by the trick and open the attached file as instructed, a fake Apple account login page will appear in your browser.
Once "logged in" via the fake page, you will be taken to a second fake form that asks for identifying information and credit card details.
After clicking "verify" on the second fake form, you will be transported to the genuine Apple website and may remain unaware - at least for a little while - that your information is now in the hands of fraudsters.
Armed with the stolen data, the criminals can commit credit card fraud and identity theft. They can also hijack your real Apple account and use it for their own illegal purposes.
Apple, or other legitimate companies, will never ask customers to provide personal and financial information via an insecure HTML form contained in an email attachment. Scammers are more often using fake forms sent via email attachments rather than links to fake websites in an apparent attempt to bypass browser phishing warnings.
Scammers use FBI names
The FBI continues to be used by scammers by using FBI officials’ names and titles in online fraud schemes. Although there are different variations of these schemes, recipients are typically notified they have received a large sum of money.
The latest round of e-mails uses the name of new FBI Director James B. Comey.
Some of the e-mails continue to use the alleged “Anti Terrorist & Monetary Crimes Division” of the FBI. All e-mails encourage the recipient to send money for various reasons.
Do not respond. These e-mails are a hoax.
Neither government agencies nor government officials send unsolicited e-mail to members of the public. United States government agencies use the legal process to contact individuals.
You should not respond to any unsolicited e-mails or click on embedded links in these messages because they may contain viruses or malicious software.
If you have received a message that claims to be from the FBI, disregard its instructions and file a complaint at www.IC3.gov.
Beta Bot Malware Blocks Users Anti-virus Programs
There is a new type of malware known as Beta Bot. Cyber criminals use Beta Bot to target financial institutions, e-commerce sites, online payment platforms, and social networking sites to steal sensitive data such as log-in credentials and financial information.
Beta Bot blocks computer users’ access to security websites and disables anti-virus programs, leaving computers vulnerable to compromise.
Beta Bot infection routes include a fake but official looking Microsoft Windows message box named “User Account Control” that requests a user’s permission to allow the “Windows Command Processor” to modify the user’s computer settings.
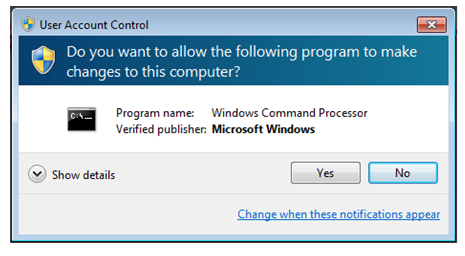
If the user complies with the request, the hackers are able to extract data from the computer. Beta Bot is also spread via USB thumb drives or online via Skype, where it redirects the user to compromised websites.
Although Beta Box masquerades as the “User Account Control” message box, it is also able to perform modifications to a user’s computer. If the above pop-up message or a similar prompt appears on your computer and you did not request it or are not making modifications to your system’s configuration, do not authorize “Windows Command Processor” to make any changes.
To remove the Beta Bot infection run a full system scan with up-to-date anti-virus software on the infected computer. If Beta Bot blocks access to security sites, download the latest anti-virus updates or a whole new anti-virus program onto an uninfected computer, save it to a USB drive and load and run it on the infected computer.
It is advisable to subsequently re-format the USB drive to remove any traces of the malware.
Spam: Delivering Malware and Advertising Dangerous Counterfeit Goods
Cyber criminals have long used spam (unsolicited e-mails, usually containing links to websites selling counterfeit goods) as a method to make money and infect computers with malicious software (malware.)
Spammers can send billions of these e-mails daily and some of them contain malware designed to steal usernames and passwords for online banking websites and harvest personal information such as names, addresses, or social security numbers.
Spam often takes the form of advertisements for illegal or counterfeit products. Buying these products is potentially harmful to the health and wellness of the purchaser because they are often low-quality or made with inferior materials.
Counterfeit drugs are not only less potent than the real drugs, but are also unregulated and potentially dangerous. Many contain unknown ingredients that can interact badly with other medications and cause serious or life-threatening side effects.
Cyber criminals can also send spam e-mails that seem to be from a trusted individual such as a bank representative, a website administrator, or an employee of a company. These e-mails often look like they come from the original source, but may have misspelled e-mail or website addresses. These e-mails try to get personal or financial information from the targeted recipients.
Cyber criminals are beginning to turn to other methods to deliver spam. Users of social media and social networking sites have begun to receive spam messages that often appear to be sent from trusted individuals or friends. Mobile devices are also becoming a target for spam and malware, usually being delivered through malicious applications. Cyber criminals can use this mobile malware to send text messages or harvest information about the phone or from the recipient’s contact list.
If you receive an e-mail that appears to be from a trusted source but are asked for personal or financial information, do not respond.
• Report the e-mail by calling or e-mailing the company’s customer service representatives. If the e-mail you are questioning is from your bank or credit card company, use the phone number on the statements you receive or the back of the credit card to get in touch
• Never respond to e-mails asking for personal or financial information unless you ensure they are legitimate
• Do not purchase products from spam e-mails, since they are very likely counterfeit and can be dangerous or deadly
• If you receive a spam e-mail or message on social media or social networking websites, delete it immediately and do not click any of the provided links. These can contain malware that can take control of your computer and steal personal information.
Pirated Software May Contain Malware
You decide to order some software from an unknown online seller. The price is so low you just can’t pass it up. Whether you’re downloading it or buying a physical disc, the odds are good that the product is pirated and laced with malicious software, or malware.
Is Your Software Pirated?
Possible signs of what to look for:
• No packaging, invoice, or other documentation...just a disc in an envelope
• Poor quality labeling on the disc, which looks noticeably different than the labeling on legitimate software
• Software is labeled as the full retail version but only contains a limited version
• Visible variations (like lines or differently shaded regions) on the underside of a disc
• Product is not wrapped correctly and is missing features like security tape around the edges of the plastic case
• Typos in software manuals or pages printed upside down
• User is required to go a website for a software activation key (often a ploy to disseminate additional malware)
Pirated software can be obtained from unknown sellers and even from peer-to-peer networks. The physical discs can be purchased from online auction sites, less-than-reputable websites, and sometimes from street vendors and kiosks. Pirated software can also be found pre-installed on computers overseas, which are ordered by consumers online and then shipped to your country.
Who’s behind this crime? Criminals, hackers and hacker groups, and even organized crime rings.
And the risks to unsuspecting consumers? For starters, the inferior and infected software may not work properly. Your operating system may slow down and fail to receive critical security updates.
But the greater danger comes from potential exposure to criminal activity—like identity theft and financial fraud—after malware takes hold of your system.
Software Buying Tips for Consumers
• When buying a computer, always ask for a genuine, pre-installed operating system, and then check out the software package to make sure it looks authentic.
• Purchase all software from an authorized retailer. If you’re not sure which retailers are authorized, visit the company website of the product you’re interested in.
• Check out the company’s website to become familiar with the packaging of the software you want to buy.
• Be especially careful when downloading software from the Internet, an increasingly popular source of pirated software. Purchase from reputable websites.
• Before buying software off the beaten path, do your homework and research the average price of the product. If a price seems too good to be true, it’s probably pirated.
Some very real dangers:
• Once installed on a computer, malware can record your keystrokes (capturing sensitive usernames and passwords) and steal your personally identifiable information (including Social Security numbers and birthdates), sending it straight back to criminals and hackers. It can also corrupt the data on your computer and even turn on your webcam and/or microphone.
• Malware can spread to other computers through removable media like thumb drives and through e-mails you send to your family, friends, and professional contacts. It can be spread through shared connections to a home, business, or even government network. Criminals can also use infected computers to launch attacks against other computers or against websites via denial of service attacks.
If you think you may have purchased pirated software or if you have information about sellers of pirated software, submit a tip to the Internet Crime Complaint Center.
Cyber Criminals Using Photo-Sharing Programs to Compromise Computers
The FBI has seen an increase in cyber criminals who use online photo-sharing programs to perpetrate scams and harm victims’ computers. These criminals advertise vehicles online but will not provide pictures in the advertisement.
They will send photos on request. Sometimes the photo is a single file sent as an e-mail attachment, and sometimes the victim receives a link to an online photo gallery.
The photos can often contain malicious software that infects the victims” computer, directing them to fake websites that look nearly identical to the real site where they originally saw the advertisement.
The cyber criminals run all aspects of these fake websites, including “tech support” or “live chat support,” and any “recommended” escrow services. After the victim agrees to purchase the item and makes the payment, the criminals stop responding to correspondence. The victims never receive any merchandise.
The FBI urges consumers to protect themselves when shopping online. Here are a few tips for staying safe:
• Be cautious if you are on an auction site and lose an auction and the seller contacts you later saying the original bidder fell through.
• Make sure websites are secure and authenticated before you purchase an item online. Use only well-known escrow services.
• Research to determine if a car dealership is real and how long it has been in business.
• Be wary if the price for the item you’d like to buy is severely undervalued; if it is, the item is likely fraudulent.
• Scan files before downloading them to your computer.
• Keep your computer software, including the operating system, updated with the latest patches.
• Ensure your anti-virus software and firewalls are current – they can help
prevent malware infections.
Spear-Phishing Attack Targeting the Petroleum Industry
The following scam targets petroleum companies. The scammers registered domain names closely resembling the domain names of the victim companies that were slightly misspelled. The scammers then sent targeted e-mails to individuals who were identified as having the ability to initiate a wire transfer within the company.
The e-mails appeared legitimate, were sent to the correct person at the company, and had contact information for the requester (usually someone in the company with the authority to request a transfer).
The victim company contacted the requestor at the number provided in the e-mail (instead of using information contained in an internal directory) and provided him/her with the information and documents required to initiate the transfer.
The perpetrator completed the form and initiated the wire transfer.
A variation of this scheme involved perpetrators creating a domain name similar in spelling to a victim company’s sub-contractor domain. The perpetrator then e-mailed the individual in charge of initiating payments to that sub-contractor and informed him/her due to various reasons, the sub-contractor needed to change the account information for all payments initiated to the sub-contractor.
The e-mail contained the name of a legitimate person at the sub-contractor, but provided a number belonging to the perpetrator. The company called the perpetrator to verify the account change and changed the payment information. The company was then contacted by its sub-contractor about delinquent payments.
Because of the increased number of spear-phishing attacks reported recently to the IC3, on June 25, 2013, the IC3 released a PSA educating consumers on spear-phishing.
The PSA is available at
http://www.ic3.gov/media/2013/130625.aspx.
Sextortion Scam
There have been a lot of complaints over the last couple of years regarding an online sextortion scam capitalizing on social media websites and technology.
Contact between the subject and victim is initiated via social media websites and/or online dating websites. Once rapport has been established, victims are asked to engage in video chat where they are enticed to expose themselves in sexually compromising situations, while their images are secretly recorded.
Subjects then threaten to make the videos available to all the victims’ social networking friends and other online contacts unless funds, ranging in the amounts of $50 to $300, are wired to various destinations overseas.
Telecommunications Customer Phishing Attack
There have been numerous reports of phishing attacks targeting various telecommunication companies' customers. Individuals receive automated telephone calls that claim to be from the victim's telecommunication carrier.
Victims are directed to a phishing site to receive a credit, discount, or prize ranging from $300 to $500.
The phishing site is a replica of one of the telecommunication carrier's sites and requests the victims' log-in credentials and the last four digits of their Social Security numbers. Once victims enter their information, they are redirected to the telecommunication carrier’s actual website.
The subject then makes changes to the customer's account.
Remember to be cautious of unsolicited telephone calls, e-mails and text messages, especially those promising some type of compensation for supplying account information. If you receive such an offer, verify it with the business associated with your account before supplying any information.
Use the information supplied on your account statement to contact the business.Paypal Scam
There is an email message circulating that claims to be from online payment company PayPal, and it states that your PayPal account has been deleted. The message claims however, that you still have time to restore access to your deleted account by clicking a "Recover Account" button in the email.
The message warns however that the account can only be recovered "within a short period of time after deletion".
This message is not from PayPal and the claim that your account have been deleted is also untrue. The email is a phishing scam designed to trick PayPal users into divulging their login information to cybercriminals.
The scammers hope that at least some people will be momentarily panicked into believing that their account has been deleted, and will click the "recover Account" link without checking first. The scammers also add urgency by suggesting that you must act quickly if you wish to recover your account, as this further increase the likelihood that you will quickly click the link.
If you click the link you will be taken to a fake PayPal login page and asked to submit your account email address and password. You may then be automatically redirected to the genuine PayPal website. Meanwhile, the criminals operating the scam can collect your stolen account details and use them to take control of your PayPal account.
This type of scam is called Phishing and PayPal is regularly targeted. It is important to remember that PayPal will always include your real name in any notifications that it sends. Emails claiming to be from PayPal that use generic greetings such as "Dear customer" or do not include a greeting at all, should be treated as suspect.
If you receive a suspect email, do not click on any links or open any attachments that it contains. It is always safest to login to your online accounts by entering the account address into your browser address bar rather than by clicking a link in an email.
Free Ipad
There is a message currently being spammed out to Facebook Walls all over the network, that claims users can get hold of a free iPad by following a link in the post.
According to the message, a particular online store has malfunctioned so that those who order an iPad on the site will have it sent to them free of charge. They claim the site “forgot" to include a payment page.
If you fall for this scam and click the link you will be taken to a fake webpage designed to look like a real Facebook "Events" Page. The page comes complete with Facebook colour scheme and layout and has a selection of clearly fake comments from equally fake users who claim that they have already received their free iPad.
The "malfunctioning store" claim is not mentioned again. Instead, the fake site displays the following message:
To participate in our iPad-3 quality test please Click here.
All participants will receive a free iPad-3 after sign up. Participants w ill be required to submit a final product review after two weeks of optimal product use.
Participant must be 18 years or older.
However if you click the link you will be taken to yet another third party website where you are told you must complete one or more surveys before being eligible for the free iPad sign up.
However, no matter how many surveys you complete, you will never get access to the elusive "sign-up" page.
The iPad "quality test" mentioned does not exist and you will never receive a free iPad as promised. If you have been tricked into participating in the fake surveys, you may have inadvertently subscribed to expensive SMS "services" charged at several dollars per text, or you may have given your personal and contact details when signing up to suspect online “offers” all in the hope of getting your free iPad or winning another prize.
The scammers who set up these schemes earn a commission through a dubious affiliate marketing system each and every time someone completes an "offer" or "survey".
If you see one of these fake messages, just delete it and do not follow any links that it may contain.
Ransomware
A new extortion technique is being used by cyber-criminals using the Citadel malware platform to deliver Reveton ransomware. The latest version of the ransomware uses the name of the Internet Crime Complaint Center to frighten victims into sending money to the scammers.
In addition to instilling a fear of prosecution, this version of the malware also claims that the user’s computer activity is being recorded using audio, video, and other devices.
It lures the victim to a drive-by download website, at which time the ransomware is installed on the user's computer. Once installed, the computer freezes and a screen is displayed warning the user they have violated United States Federal Law.
The message further declares that a law enforcement agency has determined that a computer using the victim's IP address has accessed child pornography and other illegal content.
To unlock the computer, the user is instructed to pay a fine using prepaid money card services. The geographic location of the user's PC determines what payment services are offered. In addition to the ransomware, the Citadel malware continues to operate on the compromised computer and can be used to commit online banking and credit card fraud.
This is not a legitimate communication from the IC3, but rather is an attempt to extort money from the victim. If you have received this or something similar do not follow the payment instruction.
It is suggested that you:
• File a complaint at www.IC3.gov.
• Keep operating systems and legitimate antivirus and antispyware software updated.
• Contact a reputable computer expert to assist with removing the malware.
Gmail Scam
An email circulating claims to be from Google's webmail service, Gmail, account holders are required to update their account details by clicking a link and filling in a verification form. If you don't, the message claims you will find that your Gmail accounts are permanently deleted. The message comes complete with a Gmail logo and copyright notice.
However, the email is not from Gmail and users will not lose their accounts if they fail to follow the link and update their details. Users who fall for the scam and click the link will be taken to a fake Gmail login page, which has been constructed so that it looks very similar to a real Gmail page.
After providing their login details, victims will be then taken to another fake page that asks them to provide their phone numbers.
Next, victims will be taken to yet another fake page and asked to provide login details for any alternative email addresses they may have.
After providing all the requested de tails, users will be automatically redirected to the real Gmail website. However all of the information they have provided will end up in the hands of scammers who will use it to hijack the real webmail accounts belonging to their victims.
The compromised accounts can then be used to launch more spam and scam campaigns in the name of the victims. The scammers may also use the stolen phone numbers for further illegal activities.
Email account phishing attacks like this one are very common and take many forms. Be very wary of any unsolicited email that claims that you must follow a link or reply to provide login information and other personal information. Legitimate email service providers will not ask users to provide such information via a generic email message.
Phishing Scam
The emails are phishing scams designed to trick users into submitting their email account login details to cybercriminals.
These spam emails warn recipients that their webmail accounts will be closed if the account is not updated or re-validated within a specified time frame. Many of the messages instruct users to confirm their identity by replying to the email with the webmail account username and password and other personal information.
Beware of scam emails that attempt to trick you into sending your webmail account details to Internet criminals.
The message is not from any official webmail "support team" or help desk as claimed. Nor will user accounts be closed if the requested information is not supplied. Instead, the messages are attempts by Internet criminals to fool unsuspecting webmail users into handing over their account details.
Victims who comply with the instructions in the phishing scam emails will in fact be providing the scammers with the means to directly access their webmail accounts. Once armed with the victim's account details, the scammers can login to the webmail account, steal any personal information, and use the account for sending further spam or scam emails.
The scammers can also harvest any email addresses included in the account's contact list and add them to spammer databases.
The scammers have apparently attempted to steal information from users of any webmail service by sending out a generic message that does not name a particular service provider. The message implies that there is some central webmail administrator that oversees all webmail accounts, however this is untrue.
There are now thousands of different webmail providers both large and small. Each is independently operated and they are certainly not under the control of some central administrative entity. Generic admin messages that do not identify the name of the service provider are unlikely to be genuine.
While some providers may close inactive accounts after a specified period, they will not demand that the user provide sensitive information via email or risk losing their account within a few days. Any unsolicited email that makes such a demand is likely to be fraudulent.
You should treat as suspect any email that claims that you will lose your account if you do not provide private information via email or a website. Do not reply to such emails or click on any links.Payday Loan Scams
There have been many complaints regarding pay day loan scams over the last three years and there are ongoing new variations of the scam. The scam involves victims who are relentlessly contacted, via the telephone, at their residences and places of employment.
The subjects claim the victims are delinquent on a payday loan and must repay the loan to avoid legal consequences. The subjects use coercion techniques such as harassment, threats, and claims that they were representatives of government agencies and law firms. Only some of the victims have reported previously applying for a payday loan, others said they have never made such an application.
The subjects seem to have accurate information on the victims, including social security numbers, dates of birth, addresses, employer information, bank account numbers, names and telephone numbers of relatives and friends.
The subjects refuse to provide any details of the alleged payday loans and become abusive when questioned. Victims are threatened with legal actions, arrests and, in some cases, physical violence if they refuse to pay. Some have been told there was an outstanding warrant for their arrest.
Many reported that subjects have also harassed their relatives, friends, and employers. In a couple of instances, the subjects came to the victims’ places of employment and residences claiming to be process servers.
Over the last couple of months, the scam has evolved from just receiving telephone calls to also receiving official-looking emails supposedly from the United States Attorney. The emails reference the FBI, court proceedings, and serious allegations. Allegations include violation of federal banking regulations such as collateral check fraud, theft by deception, and fraudulently conducting electronic fund transfers.
Recipients were instructed to contact the subject within 48 hours of receiving the email.
Dating Extortion Scam
There have been reports recently regarding a scam that baits individuals into intimate online conversations and then extorts them for financial gain.
The scam was initiated after the victims met someone online, such as on a dating site, and were asked to connect via a specific online social network. Shortly after, the conversations became sexual in nature.
Later, victims received text messages, either containing their names, asking if it was them or containing a statement that indicated their names were posted on a particular website. The victims were provided a link to a page on the website that claimed they were a “cheater.”
Photos of the victims and their telephone numbers were also posted. There was an option to view and buy the posted conversations for $9. Victims were also given the option to have their names and conversations removed for $99. Some were even told that once the payment was made, the information would be removed within an hour a nd the website would not allow anyone to post anything pertaining to the victims’ names again.
However, reports do not indicate that the information was ever removed.
Smartphone Malware
The IC3 has been made aware of various malware attacking Android operating systems for mobile devices. Some of the latest known versions of this type of malware are Loozfon and FinFisher. Loozfon is an information-stealing piece of malware. Criminals use different variants to lure the victims. One version is a work-at-home opportunity that promises a profitable payday just for sending out email. A link within these advertisements leads to a website that is designed to push Loozfon on the user's device. The malicious application steals contact details from the user’s address book and the infected device's phone number.
FinFisher is a spyware capable of taking over the components of a mobile device. When installed the mobile device can be remotely controlled and monitored no matter where the Target is located. FinFisher can be easily transmitted to a Smartphone when the user visits a specific web link or opens a text message masquerading as a system update.
Loozfon and FinFisher are just two examples of malware used by criminals to lure people into compromising their devices.
Safety tips to protect your mobile device:
1. When purchasing a Smartphone, know the features of the device, including the default settings. Turn off features of the device not needed to minimize the attack surface of the device
2. Depending on the type of phone, the operating system may have encryption available. This can be used to protect the user's personal data in the case of loss or theft
3. With the growth of the application market for mobile devices, users should look at the reviews of the developer/company who published the application
4. Review and understand the permissions you are giving when you download applications
5. Passcode protect your mobile device. This is the first layer of physical security to protect the contents of the device. In conjunction with the passcode, enable the screen lock feature after a few minutes of inactivity
6. Obtain malware protection for your mobile device. Look for applications that specialize in antivirus or file integrity that helps protect your device from rogue applications and malware
7. Be aware of applications that enable Geo-location. The application will track the user's location anywhere. This application can be used for marketing, but can be used by malicious actors raising concerns of assisting a possible stalker and/or burglaries
8. Jailbreak or rooting is used to remove certain restrictions imposed by the device manufacturer or cell phone carrier. This allows the user nearly unregulated control over what programs can be installed and how the device can be used. However, this procedure often involves exploiting significant security vulnerabilities and increases the attack surface of the device. Anytime a user, application or service runs in "unrestricted" or "system" level within an operation system, it allows any compromise to take full control of the device
9. Do not allow your device to connect to unknown wireless networks. These networks could be rogue access points that capture information passed between your device and a legitimate server
10. If you decide to sell your device or trade it in, make sure you wipe the device (reset it to factory default) to avoid leaving personal data on the device
11. Smartphones require updates to run applications and firmware. If users neglect this it increases the risk of having their device hacked or compromised
12. Avoid clicking on or otherwise downloading software or links from unknown sources
13. Use the same precautions on your mobile phone as you would on your
computer when using the Internet
Triangle Credit Card Fraud
Triangle Credit Card Fraud is a common scam known to affect many on-line merchants. It has been called "Triangle Credit Card Fraud" because there are three primary parties involved or impacted by the scam. The first party is the fraudster who acts as a seller on a popular auction or marketplace site. The fraudster "sells" a product to the second party, the buyer that knows nothing about the scam.
The buyer pays the seller for the product or service. The seller then needs to deliver the product or service to the buyer and does so by placing an order with the manufacturer of the product or service to the buyer and does so by placing an order with the manufacturer of the product or service, the third party.
That order will contain the buyer’s information for shipping and stolen credit card information for billing. When the company receives the order, the billing and shipping information is all legitimate, thus it looks like an order being placed as a gift, so t he company delivers the product or service. When the card holder finds a fraudulent charge on their card, they may file a dispute with the credit card company resulting in a chargeback for the company. This scheme is often much more complex as it is often led by overseas criminals who recruit established sellers (often referred to as mules) on auction or marketplace sites to "sell" the products.
Once a sale is completed, the mule will forward the buyer information and the bulk of the money to the fraudster to place the fraudulent order. Once a mule becomes trusted, they are often allowed to recruit other mules, leading to a complex pyramid of fraudsters and mules. Through the on-line merchant community, many companies have been made aware of this scheme and have had great successes with stopping the illegal activity using fraud prevention and detection solutions as well as successful criminal prosecutions.
Private Message Scam Email
You may receive an email claiming you have received a private message. The scam emails consist of nothing more than a brief message claiming that a specified email address has sent you a private message. The emails include a link that you can click to access and read your private message.
However, the link does't open a private message but instead, it opens a fake webmail login page that asks you to sign in with your User ID and Password. The information submitted on the fake signin form will be sent to scammers and may later be used to hijack your real email account.
Complaints received indicate that, once you have fallen for the scam and submitted your login details, your email accounts are then used to send the same "Private Message" scam email to all of the people on your contact list.
After you have signed in via the fake page, you are taken to another website that tries to entice you into participating in various surveys or offers in exchange for "f ree" prizes such as iPads or laptop computers. Many of the fake "survey" pages claim that you must provide personal information including name, address and contact details, before you are eligible to receive any prizes.
Others will claim that you must submit your mobile phone number before you can claim any gifts or enter any prize draws. However, you may not realize that by providing your mobile phone number you are actually subscribing to a very expensive SMS "service" charged at several dollars per message received.
No matter how many offers or surveys you complete, or what services you subscribe to, you will never receive your promised free gift or even a genuine competition entry.
The scammers who create these fake promotions will earn commissions each and every time a victim completes an offer or participates in a survey.
Victims may also be faced with large phone bills for unwanted mobile phone services and, because they have provided name and contact details, they may be inundated with unwanted promotional emails, phone calls and junk mail.
Hotel Booking Confirmation Malware Emails
Messages claiming to be hotel room booking confirmation emails are currently being distributed to inboxes around the world.
The messages, which claim to be from online booking website, Booking.com, inform you that room reservations have been made for a specified date a few days hence and you are invited to open an attached file to view full details of the supposed reservation.
However, the emails do not contain information about a real hotel booking nor are they from Booking.com. The messages are designed to trick you into opening the attached file to find out more information about a supposed booking or purchase.
In fact, the attachment contains a trojan. Once installed, this malware can collect passwords and other sensitive information from the infected computer and relay it back to a remote server for collection and use by online criminals.
There are various versions of these malware emails so if you receive one of these fake hotel booking mes sages or similar, do not open any attachments or click on any links that it may contain just to see what it says.
This malware campaign is similar to an earlier trojan attack that used fake flight ticket confirmation emails that falsely claimed to be from several airline companies.
Free Credit Service Website
We have received many complaints regarding a particular website that is claiming to offer "free" credit services such as credit scores and credit monitoring.
Customers reported being charged a monthly service fee. However, the terms of the agreement advised that the "free" report only lasts for a limited time. At the end of the free term, the website used the customer’s supplied financial information to charge a monthly membership service ranging from $19.95 to $29.95.
The terms and agreement from the website states the following:
"For Subscription Services which include a free-trial period, if you do not cancel your free trial within the free trial period, you will be charged at the monthly rate in effect at that time for the Subscription Services for which you enrolled. Your debit or credit card (including, if applicable, as automatically updated by your card provider following expiration or change in account number) will continue to be charged each month at the applicable monthly rate unless and until you cancel the Subscription Services."
The website, according to the Better Business Bureau (BBB), has been given an F rating by the BBB for the following reasons:
• 1037 complaints filed against the business
• 8 complaints filed against the business that were not resolved
• 17 serious complaints filed against business
• Advertising issue(s) found by the BBB
Facebook Phishing And Survey Scam
There are some spam messages currently targeting Facebook users, that combine a phishing scam designed to steal Facebook login details with a typical survey scam designed to trick users into submitting their personal information in the hope of receiving free gifts or prize entries.
The messages used in the scam attempt vary considerably. In one version, you are promised access to erotic content hosted on a Facebook profile. Those who take the bait and click the link in the spam message are first taken to a seemingly genuine Facebook profile page.
However, once this profile page opens, you are immediately redirected to another page designed to look like the genuine Facebook login page. The fake login page uses a web address that includes the word "facebook" in an attempt to make it appear to be a genuine Facebook web page.
If you go ahead and enter your Facebook login details you will not be taken to the erotic content you were anticipating. Instead, you w ill be taken to yet another website that promises expensive prizes such as iPads and laptop computers in exchange for participating in a brief survey.
After you have chosen your "prize" and answered the survey questions, you are then asked to provide your full name, email address, home address and phone number, supposedly so you can be contacted should you actually win the selected prize.
Fine print on the bottom of the form notes that, by entering, users consent to all their information being shared with other parties who will send them further promotional material via email, phone, text message or post.
Some of the "surveys" require you to provide a mobile phone number that will subsequently be used to subscribe you to very expensive text messaging services charged at several dollars per text. You may thus be faced with large phone bills for unwanted mobile phone services and, because you have provided your name and contact details, you may be inundated with unwanted promotional emails, phone calls and junk mail.
However some victims have also divulged their Facebook login credentials to the criminals operating the scam. Once they have collected this information, the scammers can then login to the victims real Facebook account, lock out the genuine account holder, and use it to perpetrate further Facebook driven scam and spam attacks.
It is always safest to login to your online accounts by entering the address into your web browser rather than by clicking a link in a message.
Citadel Malware Delivers Reveton Ransomware in Attempts to Extort Money
There is a new Citadel malware platform used to deliver ransomware, named Reveton. The ransomware lures the victim to a drive-by download website, at which time the ransomware is installed on the user's computer.
Once installed, the computer freezes and a screen is displayed warning the user they have violated United States Federal Law. The message further declares the user's IP address was identified by the Computer Crime & Intellectual Property Section as visiting child pornography and other illegal content.
To unlock their computer the user is instructed to pay a $100 fine to the US Department of Justice, using prepaid money card services. The geographic location of the user's IP address determines what payment services are offered.
In addition to the ransomware, the Citadel malware continues to operate on the compromised computer and can be used to commit online banking and credit card fraud.
This is an attempt to extort money with the additional possibility of the victim’s computer being used to participate in online bank fraud. If you have received this or something similar do not follow payment instructions. It is suggested that you;
• Contact your banking institutions
• File a complaint at www.IC3.gov
Hotel Internet Connection Malware
Recent emails to us indicate an increase in cybercrime targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms.
There have been many instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product.
If you clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
It is recommended that all people who travel abroad take extra caution before updating software products on their hotel Internet connection. Checking the author or digital certificate of any prompted update to see if it corresponds to the software vendor may reveal an attempted attack.
It is worth travelers performing software updates
on laptops immediately before traveling, and that they download software
updates directly from the software vendor’s Web site if updates are
necessary while abroad.
Want to Get Paid to Drive Your Own Car?
Several people have complained about a scam involving the advertising of a company's logo on their personal vehicle while they go about their normal daily routine.
Although legitimate offers exist, those scammed reported that initial contact with the scammer was mostly through online ad postings. The posting offered an easy way to earn extra income by allowing businesses to advertise their logo on your personal vehicle through a vinyl decal or "auto wrap."
The fraudsters were using company names such as Coca Cola, Monster Energy drink, Carlsberg beer, Heineken Co., and Red Bull. People were advised they would be paid an average of $400-$600 per week in exchange for driving around with vinyl advertising signs wrapped around their vehicle. Those interested in participating were asked to provide their contact information and vehicle details.
They were promised an up-front payment, which would be sent by check or money order. The employment offer was, o f course, entirely fake. Those who fell for the scam received a check or money order for more than the promised amount. They were directed to cash it and wire the difference to a third party, who was supposed to be the graphics designer to pay for the cost of the design. The checks and money orders turned out to be counterfeit and the criminals, once again, were able to convert fraudulent checks and money orders into untraceable cash, leaving the victim responsible for the bank's losses.
Facebook/Apple Scam
According to an email message you may receive that claims to be from the Facebook CEO Mark Zuckerberg, it states you have won an Apple iPhone and an Apple iPad.
The message claims that Mark Zuckerberg has partnered with Apple to create a "one-time promotional event" and that you were randomly selected as a winner.
Supposedly, all the "winner" needs do to collect the prize is follow a link in the message and fill in a short survey.
However, the message is not from Mark Zuckerberg or from Apple and the claims that you have won Apple products is not correct and is designed to trick you into clicking a link to a scam promotional website. If you are fooled by the message and follow the link to claim your prize you will be told that you must participate in a simple survey as part of the claims process.
The supposed survey requires you to supply a mobile phone number as part of the process, however by providing your phone number you are in fact subscribing to a very expensive text messaging service that is billed at several dollars per message sent. And, if you fall for the scam and provide the requested phone number, you will be presented with even more fake surveys.
No matter how many surveys you fill out, you will never receive the promised Apple products. The scammers involved in this scam will receive commissions from affiliate marketing schemes each and every time someone completes a survey.Counterfeit Check Scam
U.S. law firms continue to be the target of scammers with a counterfeit check scheme. The scammers contact lawyers via e-mail, claiming to be overseas and requesting legal representation in collecting a debt from third parties located in the U.S.
The law firms receive a retainer agreement and a check payable to the law firm. The firm is instructed to deposit the check, take out retainer fees, and wire the remaining funds to banks in China, Korea, Ireland, or Canada. After the funds are wired overseas, the checks are determined to be counterfeit. In a slight variation of the scheme's execution, the victim law firm receives an e-mail from what appears to be an attorney located in another state requesting assistance for a client.
The client needs aid in collecting a debt from a company located in the victim law firm's state. In some cases, the name of the referring attorney and the debtor company used in the e-mail were verified as legitimate entities and were being used as part of the scheme.
The law firm receives a signed retainer agreement and a check made payable to the law firm from the alleged debtor. The client instructs the law firm to deposit the check and to wire the funds, minus all fees, to an overseas bank account. The law firm discovers after the funds are wired the check is counterfeit. Law firms should use caution when engaging in transactions with parties who are handling their business solely via e-mail, particularly those parties claiming to reside overseas.
Attorneys who agree to represent a client in circumstances similar to those described above should consider incorporating a provision into their retainer agreement that allows the attorney to hold funds received from a debtor for a sufficient period of time to verify the validity of the check.
Mystery Shopper Scam To Evaluate Wire Transfer Services
There have been recent reports of a new twist to the online employment scam. The scam involves individuals who responded to online ads or were contacted via e-mail as a result of their resume being posted on job websites.
The scammer posed as a research company and requested participants to complete a paid survey regarding services provided at wire transfer locations to improve the effectiveness of the company's money-transfer services.
Victims were hired and then mailed a cashier's check or money order. They received instructions to cash the check/money order at their local bank,keep a portion as payment, and wire the remaining amount via wire transfer to a designated recipient.
Victims were then asked to immediately e-mail their employer with the transfer number, amount wired, recipient's name and address, and the name of the wire transfer location evaluated.
Upon sending the information, victims received a questionnaire form regarding their overall wire transfer experience to complete and return. Those who did not promptly follow through with the instructions received threatening e-mails stating if they did not respond within 24 hours, their information would be forwarded to the FBI and they could face 25 years in jail.
Shortly after the transactions, victims were informed by their banks that the checks were counterfeit and were held responsible for reimbursing their banks. Most victims owed their bank over $2,500.
Timeshare Marketing Scams
Timeshare owners are being scammed out of millions of dollars by unscrupulous companies that promise to sell or rent the unsuspecting victims' timeshares.
In the typical scam, timeshare owners receive unexpected or uninvited telephone calls or e-mails from criminals posing as sales representatives for a timeshare resale company. The representative promises a quick sale, often within 60-90 days.
The sales representatives often use high-pressure sales tactics to add a sense of urgency to the deal. Some victims have reported that sales representatives pressured them by claiming there was a buyer waiting in the wings, either on the other line or even present in the office. Timeshare owners who agree to sell are told that they must pay an upfront fee to cover anything from listing and advertising fees to closing costs. Many victims have provided credit cards to pay the fees ranging from a few hundred to a few thousand dollars.
Once the fee is paid, timeshare owners report that the company becomes evasive – calls go unanswered, numbers are disconnected, and websites are inaccessible. In some cases, timeshare owners who have been defrauded by a timeshare sales scheme have been subsequently contacted by an unscrupulous timeshare fraud recovery company as well. The representative from the recovery company promises assistance in recovering money lost in the sales scam.
Some recovery companies require an up-front fee for services rendered while others promise no fees will be paid unless a refund is obtained for the timeshare owner.
There have been some instances where people involved with the recovery company also have a connection to the resale company, raising the possibility that timeshare owners are being scammed twice by the same people. If you are contacted by someone offering to sell or rent your timeshare, below are tips you can use to avoid becoming a victim of a timeshare scheme:
• Be wary if a company asks you for up-front fees to sell or rent your timeshare
• Read the fine print of any sales contract or rental agreement provided
• Check with the Better Business Bureau to ensure the company is reputable
Damage to Your Computer
Cyber criminals can damage your computer systems and data by changing or deleting files, wiping hard drives, or erasing backups to hide some or all of their malicious activity.
By wiping, or "zeroing out," the hard disk drives, which overwrites good data with zeros or other characters, the criminals effectively erase or alter all existing data, greatly impeding restoration.
This sort of criminal activity makes it difficult to determine whether criminals merely accessed your computer, stole information, or altered access and configuration files.
The FBI encourage businesses and individuals to employ mitigation strategies and best practices such as:
• Implement a data back-up and recovery plan to maintain copies of sensitive or proprietary data in a separate and secure location. Backup copies of sensitive data should not be readily accessible from local networks.
• Regularly mirror and maintain an image of critical system files.
• Encrypt and secure sensitive information.
• Use strong passwords, implement a schedule for changing passwords frequently, and do not reuse passwords for multiple accounts.
• Enable network monitoring and logging where feasible.
• Be aware of social engineering tactics aimed at obtaining sensitive information.
• Securely eliminate sensitive files and data from hard drives when no longer needed or required.
Remember, it is better to take preventative measures now, than try to deal with the problem after it has occurred.
Also remember Valentines Day is coming up. Scammers will be taking full advantage of it on dating sites, e-cards and florists. Be especially alert!
Facebook Worm
A computer worm that has traditionally targeted the financial industry has set its sights on social networking, recently stealing over 45,000 Facebook login credentials.
The worm, known as Ramnit, dates back to April 2010 and steals stored login information. Ramnit was not initially designed to harvest Facebook credentials, but the Ramnit cybercriminals have recognized the value of Facebook accounts for propagation.
It is likely that the attackers behind Ramnit are using the stolen credentials to log-in to victims' Facebook accounts and to transmit malicious links to their friends, thereby magnifying the malware's spread even further.
In addition, cybercriminals are taking advantage of the fact that users tend to use the same password in various web-based services (Facebook, Gmail, Corporate SSL VPN, Outlook Web Access, etc.) to gain remote access to corporate networks.
As communication overall has shifted from traditional mediums such as email to social networks like Facebook, malware writers likewise are adopting their victim's preferred means of communication.
People are now less likely to click a random link via email, but trust is still relatively high on Facebook. Receiving communication from a trusted contact on Facebook will have much higher click-through rates.
Victims are simply not aware that the 'trusted' Facebook account from which the communication was received, may itself have already been compromised.
Remember not to click on strange links, to report suspicious activity on the social network, and become fans of the Facebook Security Page for additional security information.
Pet Scams
Losing a pet is a devastating experience. We have received emails about scammers who are defrauding heartbroken pet owners in order to line their own pockets so we advise pet owners who have advertised a lost pet to be wary of the following pet scams. Scammers are cunning and play on pet owner's emotions. The scammers sole goal is to make some easy money and see pet owners who have lost their animals as easy targets.
The Pay-Me-First Scam occurs when the pet owner receives a phone call from a person claiming that they have the lost pet in their possession. This person asks that the reward money be sent to them before they return the pet.
If the pet owner refuses, they will often threaten to hurt the pet in order to pressure the pet owner into sending money. Once the scammer receives the money, they are never heard from again.
The Truck Driver Scam involves someone claiming to be a long-haul truck driver who tells you that he came across your pet while on his route. He then asks you to send him money so that he can send your pet back to you, or he may ask you to wire him money to board your pet until he can send your pet back with another truck driver who's heading your way.
The Tag Team Scam works when you receive a call from someone who says that they think they have your pet. After talking to you for a while and getting information about your pet, they apologize and say that they're sorry, but it turns out that it's not your pet after all.
They then give all the information about your pet to a partner. This is a set-up as in a short time, the scammer uses the information received about your pet only to have a second person call and claim to have found your pet who will then try to collect any reward money in advance.
The Airline Ticket Scam involves a scammer calling and claiming that your pet somehow ended up in another state. They ask you to send money for a kennel and an airline ticket in order for them to ship your pet back to you.
Once the pet owner sends the money, the scammer walks away with it, leaving the owner without their pet and with less money in their bank account.
The following tips may prevent you from falling victim to a pet loss scam:
1. If you must place an ad, include only essential information. Refrain from providing information about unique markings or physical attributes.
2. If you get a call from someone who claims to be out-of-state, ask them for a phone number where you can call them back.
3. If a caller claims to have your pet in their possession, ask them to describe something about the pet that wouldn’t be visible in pictures which may have been posted.
4. Never wire money to anyone you don’t know.
Popular Passwords
An Internet site who manages passwords recently posted an article relating to the lack of secure passwords being used which may be a factor in data breaches — past, present, and future.
One reason for the lack of security is the amount of passwords a user is required to remember to access the many databases, applications, multiple networks, etc., used on a daily basis.
Sharing passwords among users in a workplace is becoming a common theme to continue the flow of operations. Users have prioritized convenience over security when establishing passwords. The article provided a list of millions of stolen passwords posted on-line by hackers and ranked the top 25 common passwords.
1. password
2. 123456
3. 12345678
4. qwerty
5. abc123
6. monkey
7. 1234567
8. letmein
9. trustno1
10. dragon
11. baseball
12. 111111
13. iloveyou
14. master
15. sunshine
16. ashley
17. bailey
18. passw0rd
19. shadow
20. 123123
21. 654321
22. superman
23. qazwsx
24. michael
25. football
Do any of these look familiar?
A strong password is an important protection to help you have safer online transactions. Here are some steps you can take to create a strong password. Some or all might help protect your online transactions:
• Length. Make your passwords long with eight or more characters
• Complexity. Include letters, punctuation, symbols, and numbers. Use the entire keyboard, not just the letters and characters you use or see most often. The greater the variety of characters in your password, the better. However, password hacking software automatically checks for common letter-to-symbol conversions, such as changing "and" to "&" or "to" to "2."
• Variation. To keep strong passwords effective, change them often. Set an automatic reminder for yourself to change your passwords on your email, banking, and credit card websites about every three months
• Variety. Don't use the same password for everything. Cybercriminals steal passwords on websites that have very little security, and then they use that same password and user name in more secure environments, such as banking websites.
SMS Scams
Recent emails from newsletter subscribers suggest that advance fee scammers are increasingly using phone text (SMS) messages as a means of gaining new victims.
These unsolicited text messages claim that your mobile phone number has been selected as the winning entry in a lottery or promotion. The texts claim that you have therefore won a substantial sum of money or, in some versions, a valuable prize such as a car.
To claim your prize, you are instructed to call or email using contact details included in the message.
However, the lottery or promotions mentioned in the text messages do not exist and there is no prize. The promised prize is simply the bait used to get you to contact the criminals responsible for the scam.
If you fall for the scam and make contact as instructed, you will soon be asked to send money, supposedly in order to allow the release and transfer of the prize. The scammers will claim that this money is required to cover expenses such as tax, legal, insurance or banking fees.
They will insist that these fees cannot be deducted from the prize itself. If you comply and send the first fee requested, the scammers will invent other "expenses" that must be paid in advance before the prize can be handed over.
Requests for money are likely to continue until you realize that you are being scammed or simply run out of money to send. During the course of the scam, you may also be asked to provide a substantial amount of personal and financial information, supposedly as a means of proving identity and allowing transfer of the "prize money". The scammers may subsequently use this information to steal your identity.
Advance fee lottery scams are certainly not new and have been around for many years. Advance fee scammers use a variety of methods to reach potential victims, including email, surface mail, fax, social networking and, now SMS.
The scammers often claim that the prize or promotion is connected to a high-profile company such as Nokia or Microsoft. The scammers use the names, and, sometimes, the logos and trademarks of such companies without permission as a means of making their claims seem more legitimate.
You need to be very cautious of any unsolicited message that claims that you have won money or a prize in some form of lottery or promotion that you have never even entered.
Be wary of any message in any format that claims that your name, phone number or email address has been randomly selected as the winner of a substantial prize. Genuine lotteries do not operate in this manner. If you receive such a scam message, do not reply or respond to the scammers in any way.
Holiday Shopping Season Tips
As the holiday season approaches, the FBI reminds shoppers to beware of cyber criminals and their aggressive and creative ways to steal money and personal information.
Scammers use many techniques to fool potential victims including fraudulent auction sales, reshipping merchandise purchased with a stolen credit card, sale of fraudulent or stolen gift cards through auction sites at discounted prices, and phishing e-mails advertising brand name merchandise for bargain prices or e-mails promoting the sale of merchandise that ends up being a counterfeit product.
Fraudulent Classified Ads or Auction Sales
Internet criminals post classified ads or auctions for products they do not have. If you receive an auction product from a merchant or retail store, rather than directly from the auction seller, the item may have been purchased with someone else's stolen credit card number.
Contact the merchant to verify the account used to pay for the item actually belongs to you. Shoppers should be cautious and not provide credit card numbers, bank account numbers, or other financial information directly to the seller. Fraudulent sellers will use this information to purchase items for their scheme from the provided financial account. Always use a legitimate payment service to protect purchases. Diligently check each seller's rating and feedback along with their number of sales and the dates on which feedback was posted. Be wary of a seller with 100% positive feedback, if they have a low total number of feedback postings and all feedback was posted around the same date and time.
Gift Card Scam
The safest way to purchase gift cards is directly from the merchant or authorized retail merchant. If the merchant discovers the card you received from another source or auction was initially obtained fraudulently, the merchant will deactivate the gift card number, and it will not be honored to make purchases.
Phishing and Social Networking
Be wary of e-mails or text messages you receive indicating a problem or question regarding your financial accounts. In this scam, you are directed to follow a link or call the number provided in the message to update your account or correct the problem.
The link actually directs the individual to a fraudulent Web site or message that appears legitimate; however, any personal information you provide, such as account number and personal identification number (PIN), will be stolen. Another scam involves victims receiving an e-mail message directing the recipient to a spoofed Web site. A spoofed Web site is a fake site or copy of a real Web site that is designed to mislead the recipient into providing personal information. Consumers are encouraged to beware of bargain e-mails advertising one day only promotions for recognized brands or Web sites. Fraudsters often use the hot items of the season to lure bargain hunters into providing credit card information. The old adage "if it seems too good to be true" is a good barometer to use to legitimize e-mails. Along with on-line shopping comes the growth of consumers utilizing social networking sites and mobile phones to satisfy their shopping needs more easily. Again, consumers are encouraged to beware of e-mails, text messages, or postings that may lead to fraudulent sites offering bargains on brand name products.
Tips
Here are some tips you can use to avoid becoming a victim of cyber fraud:
• Do not respond to unsolicited (spam) e-mail
• Do not click on links contained within an unsolicited e-mail
• Be cautious of e-mail claiming to contain pictures in attached files, as the files may contain viruses. Only open attachments from known senders. Always run a virus scan on attachment before opening
• Avoid filling out forms contained in e-mail messages that ask for personal information
• Always compare the link in the e-mail to the web address link you are directed to and determine if they match
• Log on directly to the official Web site for the business identified in the e-mail, instead of "linking" to it from an unsolicited e-mail. If the e-mail appears to be from your bank, credit card issuer, or other company you deal with frequently, your statements or official correspondence from the business will provide the proper contact information
• Contact the actual business that supposedly sent the e-mail to verify that the e-mail is genuine
• If you are requested to act quickly or there is an emergency, it may be a scam. Fraudsters create a sense of urgency to get you to act impulsively
• If you receive a request for personal information from a business or financial institution, always look up the main contact information for the requesting company on an independent source (phone book, trusted internet directory, legitimate billing statement, etc.) and use that contact information to verify the legitimacy of the request
• Remember if it looks too good to be true, it probably is.
Twilight Scams
With all of the hype surrounding the movie Twilight: Breaking Dawn (part 1), hackers are taking advantage of people doing Internet searches for Twilight-related information.
If you are doing a Web search you will see results such as “nude pictures of Taylor Lautner,” “Robert and Kristin kissing,” and “Twilight true love.” Clicking these links can infect your computer, tablet, or smartphone with viruses or keyloggers.
There will be more of this malware as the excitement around the movie grows.
This isn’t the first time fans of Twilight Saga have been the target of a scam. In April, 2011 a Twilight scam spread virally on Facebook so that when Twilight fans tried to play Twilight: Breaking Dawn, they discovered they first had to “like” the game, and then it would get posted to their Facebook wall, spreading to their friends.
The victims were then asked to okay a Facebook application to access their account and to complete a form that asked for personal information.
So be suspicious of links like these and verify each application before giving it additional permissions on Facebook.
Here are other signs of scams that could surround the Twilight hype:
1. Fake online sneak previews or complete downloads of the movies, usually accompanied by fake comments from supposedly delighted users
2. Page links that lead to surveys that collect personal details for spammers, or insist users first download a toolbar or special viewer, either of which, in reality, installs spyware, a virus or fake anti-virus software onto computers
3. Phony digital (ebook) versions of the series, again leading to the kind of scams outlined in the point above
4. Subject headings for web pages and emails with some
sort of sensational claim about one of the characters, luring curious fans
to visit or open attachments.
Free Airline Tickets Scam
It's a good rule of thumb that whenever any of your Facebook friends tell you about a great free offer, it's probably a scam. The latest hot freebie scam doing the Facebook rounds is the free Southwest Airlines tickets scam.
The messages are being left on people's walls as though they are from Facebook friends.
“Aweet! i just got 2 free flight vouchers from Southwest Air to fly to any destination i can think of lmao!,” one message says. “i didnt believe it would work but it was, got it here..[LINK] try for yourself i just figured i would share with everyone.”
The fact is Southwest isn't giving away any free tickets. If you fall for the scam and click on the link, you will be taken to a site that appears to be the official Southwest site, but is actually a fake site set up by the scammer.
When you get to the site, you'll be asked to allow installation of third-party software to allow you to register for the tickets. If you agree, you will download malware that can access your profile and post messages from your account.
A variation of the scam leads you through a maze of multiple surveys, resulting in no tickets for your efforts. Southwest alerted customers through social media Monday, warning them of the fraud.
The scams have a common theme and every few weeks resurface with a slight variation.
Last month the hot Facebook scam was the promise of free giftcards from Starbucks. It read along the lines of “Facebook Users!, Starbucks is gifting away new giftcards! Rush, Dont waste any time. Here is webpage (link) There just 241 left!!!
The rest of the scam is pretty much the same and entices you into downloading an application that gives the scammer access to your Facebook account.
According to Softpedia.com, a recent bust by the FBI
showed a cybercrook gang took in $14 million off a similar scam.
Online Holiday Scams to Avoid
McAfee has just released the "dozen most dangerous online scams" which is a timely reminder of what to look for and avoid.
1. Mobile malware: More of us are using our phones for shopping, to research products or to redeem coupons. McAfee says Android phones are "most at risk," citing "a 76 percent increase in malware targeted at Android devices in the second quarter of 2011 over the first, making it the most targeted smartphone platform."
McAfee also says new malware "has recently been found that targets QR codes, a digital barcode that consumers might scan with their smartphone to find good deals on Black Friday and Cyber Monday, or just to learn about products they want to buy."
2. Malicious mobile apps: "These are mobile apps designed to steal information from smartphones, or send out expensive text messages without a user’s consent. Dangerous apps are usually offered for free, and masquerade as fun applications, such as games. For example, last year, 4.6 million Android smartphone users downloaded a suspicious wallpaper app that collected and transmitted user data to a site in China."
3. Phony Facebook promotions and contests: "Who doesn’t want to win some free prizes or get a great deal around the holidays? Unfortunately, cyber scammers know that these are attractive lures and they have sprinkled Facebook with phony promotions and contests aimed at gathering personal information." One recent scam promised two free airline tickets — something that sounds appealing at this time of year especially — "but required participants to fill out multiple surveys requesting personal information."
4. Scareware, or fake antivirus software: We've seen lots of examples this year. "Scareware is the fake antivirus software that tricks someone into believing that their computer is at risk — or already infected — so they agree to download and pay for phony software." McAfee says it's one of "the most common and dangerous Internet threats today, with an estimated 1 million victims falling for this scam each day."
5. Holiday screensavers: Ah yes, we love our screensavers for special times of the years like Christmas. But some of the free ones are loaded with more than holiday cheer. "A recent search for a Santa screensaver that promises to let you 'fly with Santa in 3D' is malicious," McAfee says. "Holiday-themed ringtones and e-cards have been known to be malicious too."
6. Mac malware: Those two words wouldn't have even been put together in the same sentence a few years ago. But, as McAfee correctly says, "with the growing popularity of Apple products, for both business and personal use, cyber criminals have designed a new wave of malware directed squarely at Mac users." McAfee Labs says as of a year ago, there were "5,000 pieces of malware targeting Macs, and this number is increasing by 10 percent month on month."
7. Holiday phishing scams: "Cyber scammers know that most people are busy around the holidays so they tailor their emails and social messages with holiday themes in the hopes of tricking recipients into revealing personal information."
A "common holiday phishing scam is a phony notice from UPS, saying you have a package and need to fill out an attached form to get it delivered. The form may ask for personal or financial details that will go straight into the hands of the cyber scammer."
Bank phishing scams "continue to be popular and the holiday season means consumers will be spending more money — and checking bank balances more often. From July to September of this year, McAfee Labs identified approximately 2,700 phishing URLs per day."
And, "smishing" — phishing by text message, usually involving banking — is also a growing problem. "Scammers send their fake messages via a text alert to a phone, notifying an unsuspecting consumer that his bank account has been compromised. The cybercriminals then direct the consumer to call a phone number to get it re-activated — and collects the user’s personal information including Social Security number, address and account details."
8. Online coupon scams and offers: Whether you're an extreme couponer or an occasional one, the season is rife with good online offers — and malicious ones. "Scammers know that by offering an irresistible online coupon, they can get people to hand over some of their personal information," McAfee says. "One popular scam is to lure consumers with the hope of winning a 'free' iPad. Consumers click on a 'phishing' site, which can result in email spam and possibly dealing with identify theft." Another is that "consumers are offered an online coupon code and once they agree, are asked to provide personal information, including credit-card details, passwords and other financial data."
9. Mystery shopper scams: "There have been reports of scammers sending text messages to victims, offering to pay them $50 an hour to be a mystery shopper, and instructing them to call a number if they are interested. Once the victim calls, they are asked for their personal information, including credit card and bank account numbers."
10. Hotel "wrong transaction" malware emails: "In one recent example, a scammer sent out emails that appeared to be from a hotel, claiming that a 'wrong transaction' had been discovered on the recipient’s credit card. It then asked them to fill out an attached refund form. Once opened, the attachment downloads malware onto their machine."
11. “It” gift scams: Looking for the kind of gift that might sell out quickly this year? "When a gift is hot, not only do sellers mark up the price, but scammers will also start advertising these gifts on rogue websites and social networks, even if they don’t have them," says McAfee. "So, consumers could wind up paying for an item and giving away credit card details only to receive nothing in return. Once the scammers have the personal financial details, there is little recourse."
12. “I’m away from home” scammers: You know this by now, or should: "Posting information about a vacation on social networking sites could ... be dangerous. If someone is connected with people they don’t know on Facebook or other social networking sites, they could see their post and decide that it may be a good time to rob them. Furthermore, a quick online search can easily turn up their home address."
Protecting yourself:
Here are some of McAfee's tips on staying safe in general, but especially in the weeks ahead:
•"Only download mobile apps from official app stores, such as iTunes and the Android Market, and read user reviews before downloading them."
•"Be extra vigilant when reviewing and responding to emails."
•"Watch out for too-good-to-be-true offers on social networks (like free airline tickets). Never agree to reveal your personal information just to participate in a promotion."
•"Don’t accept requests on social networks from people you don’t know in real life. Wait to post pictures and comments about your vacation until you’ve already returned home
Gift Card Scam
The cards are attractive targets for fraud because, unlike credit or debit cards, there's no identifying name attached to them - only strings of numbers.
Most commonly, thieves case racks of gift cards in stores, writing down the identifying numbers or using a scanner to lift information from their magnetic strips.
Armed with the data, they head home to their computers and wait for customers to buy the cards. They repeatedly check websites that display gift card balances, which tell them when the card is activated. As soon as it's activated, they spend the balance in an online shopping spree.
In a more sophisticated variation of the scam, the thieves also steal a blank card to create a counterfeit card they can use in a store as well as online. In both cases, customers often don't find out their gift is null and void until the intended recipient receives it, weeks or months after the original purchase.
The scams are possible because most retailers simply don't package their gift cards well enough to conceal the identifying numbers And while the greatest risk lies with so-called "closed-loop" cards that can only be used at a single store such as Target or Best Buy, thieves can also target "open-loop" cards issued by credit card companies. They swap activation stickers attached to the outside packaging, so that a consumer buys one card but activates the one possessed by the scam artists.
Other scammers target consumers who buy gift cards from online exchanges such as PlasticJungle or auction sites such as eBay.
Some thieves try writing down their card's numeric identifiers, selling the card to the discount website and then racing to spend the card's balance before a new buyer has the chance to do so.
Tips for avoiding gift cards scams
• Don't buy gift cards displayed prominently within the store. Ask sales clerks to sell you cards from the back room or behind the customer service desk
• Examine cards and packaging for signs of tampering. Don't buy a card where the coating covering the PIN number has been scratched away or the activation sticker isn't firmly affixed
• Spend the gift card as soon as possible. Don't put the card in a drawer for months. The longer consumers take to spend their gift cards, the more time thieves have to do it for them
• Beware of online exchanges and auction sites. The
Federal Trade Commission advise against buying cards from online exchanges
or auction sites because of the possibility of buying stolen cards. Instead,
buy cards directly from retailers
AT&T Phishing Scam
You may receive an email that claims to be from US telecommunications giant, AT&T, and states that "due to congestion" all unused AT&T accounts are set to be shut down.
According to the message, if you wish to keep your account you must verify it by replying with your username and password details.
Please note that the email is not from AT&T and the claim that all unused accounts are about to be closed is false. The message is an attempt by criminals to trick you into divulging your account login details. If you fall for the scam and send the requested details, you will be effectively handing control of your AT&&T account to the scammers.
Once they have collected your details, the scammers can login to your compromised account, steal more personal information stored in the account's files and use the account to launch further scam and spam campaigns.
Often, the scammers use the hijacked accounts to send typical "stranded in a foreign country" scam messages to people on your contact list. Because the messages apparently come from a person that you know, you may be more inclined to believe the scammer's story and send money as requested.
AT&T will never send you an unsolicited email that expects you to reply with sensitive information such as passwords. Nor will any other legitimate Internet or telecommunications company.
If you receive one of these emails, do not reply. Do not open any attachments that the message may contain and do not click any links in the email.
Online Vehicle Scam Using Kelley Blue Book's Name
There have been several complaints reporting fraudsters for misrepresenting themselves as Kelley Blue Book (KBB) agents to swindle victims out of thousands of dollars in online vehicle purchases.
Upon finding a vehicle and making an inquiry to the seller, the complainant was told that the transaction must go through KBB's escrow-based buyer-protection plan to protect both of them.
The fraudster claimed that the protection plan would hold the buyer's money for a five-day period while they could receive and inspect the vehicle. The fraudster then sent the complainant a link, which was supposedly to the KBB website, providing details of the process.
Some people reported that the fraudster sent pictures of the vehicle as well. Once the purchase was agreed upon, the fraudster sent the complainant an official-looking e-mail, supposedly from KBB, instructing them to wire the payment to a KBB agent. Upon contacting the actual KBB company, complainants were advised that it was a scam and that KBB does not offer an escrow-based buyer-protection plan. Recent articles have been posted on the KBB website warning consumers of this particular scam.
Archive 11
- Home ›
- Scam Alerts